Read Our Data Sheets
Filter By Year:
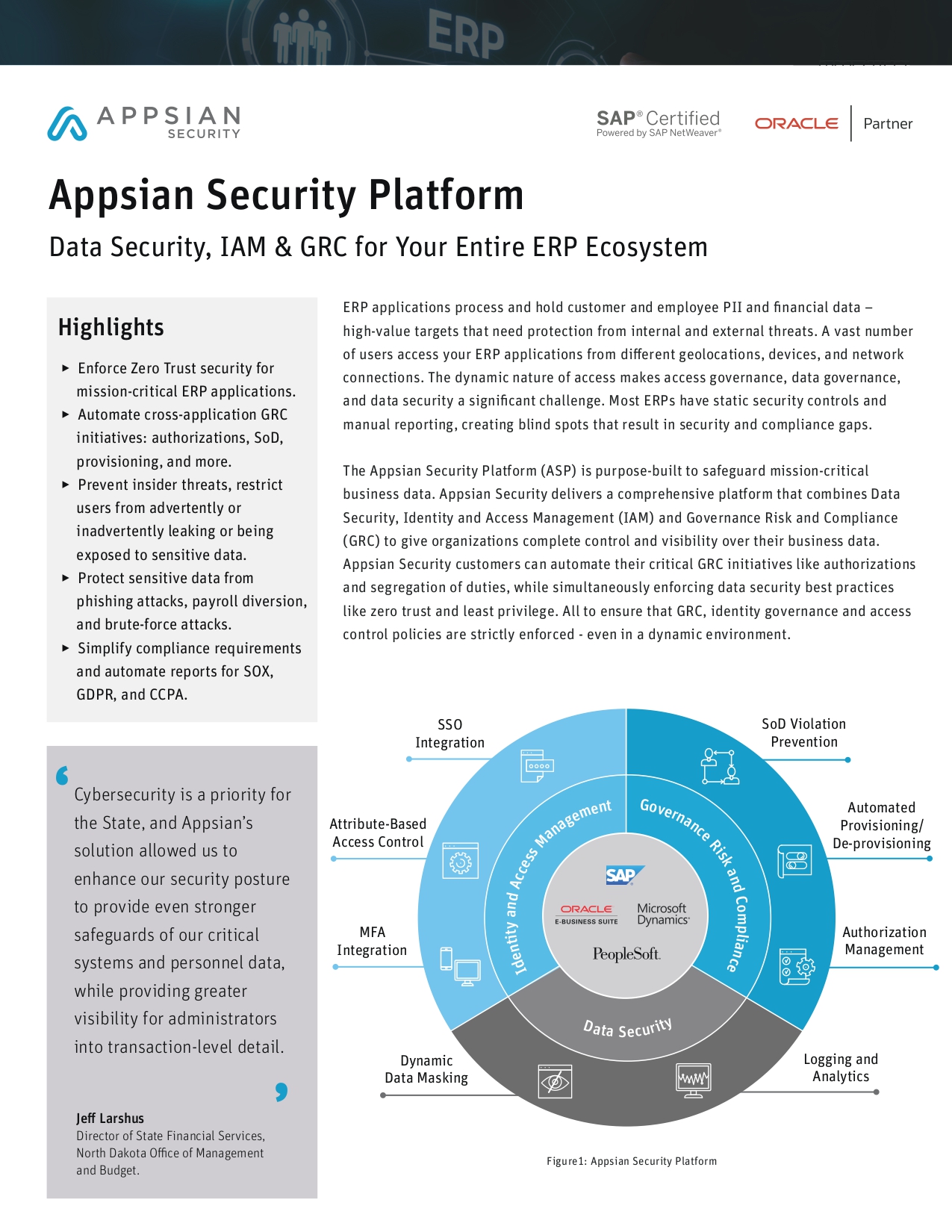
An ever-changing business application environment demands a governance and compliance solution that can keep pace.
However, what happens when user access spans not just Oracle, but multiple applications? Who is responsible for manually gathering and analyzing data to uncover conflicts? Unfortunately, access conflicts (ie SoD) are typically discovered long after any compliance violations have occurred and misappropriated funds have left the building.

Featuring visually rich, easily configurable dashboards, Appsian Real-Time Analytics answers the most critical questions that support the ongoing integrity of your sensitive business data. It is data-centric, enriched with full contextual detail.

QCloud is a Cloud-based audit service which analyzes your ERP security and Segregation of Duties (SoD). Simply login to QCloud, request an audit and the results are delivered within hours. With minimal technical effort and training required for installation, you can receive accurate audit reports whenever you want. Using QCloud, you will benefit from the in-depth knowledge of our security and audit experts, and shine a light on vulnerabilities that many people overlook.
View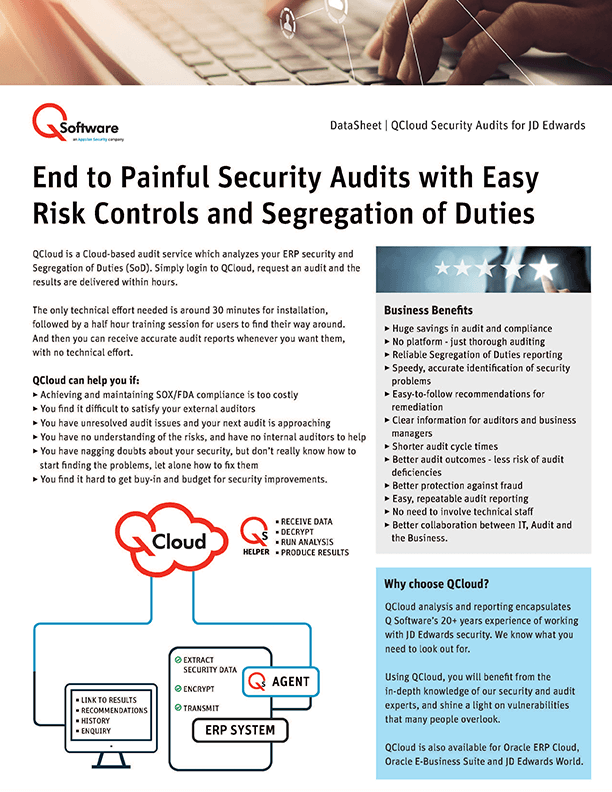
Managing security in JD Edwards can be extremely complex and time-consuming, with lots of redundant effort. Spreadsheets are prone to error, also difficult to monitor the version and changes made, leading to risks within live security table. Security Manager Pro is completely integrated into the JD Edwards environment, built on a set of custom programs and tables that enable efficient security management at Role level. Access to data can be restricted to authorized users only with complete audit-trail of changes.
View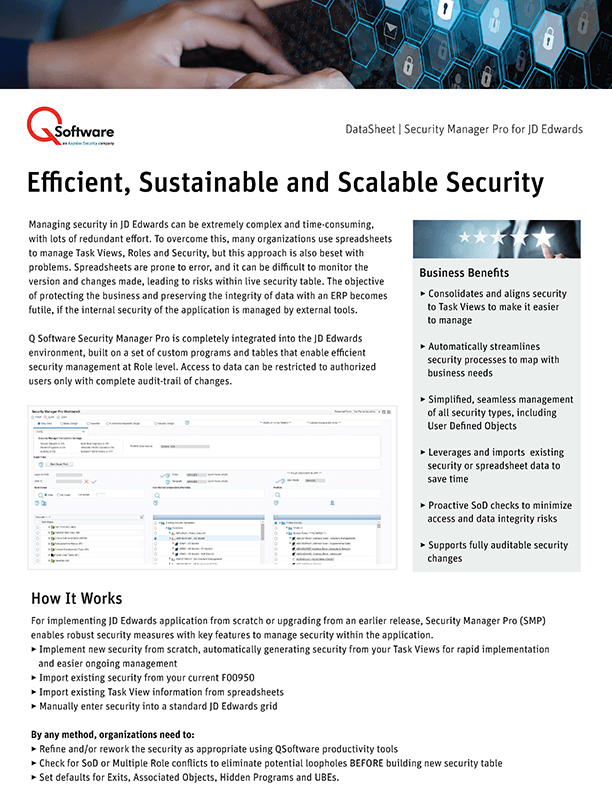
The three key approaches to ensuring an ERP system is not the subject of internal fraud are controlling access, setting up Segregation of Duties, and setting up alerts on critical data. Fraud Detector fits very well with the Q Software tools for Access control and SoD, by enabling the user to selectively set up alerts against areas of the system that are concerning. Changes to key data entities such as the Address Book or even Payroll data can be monitored, and Management informed of suspicious activity.
View
Native JD Edwards EnterpriseOne contains no functionality to help manage SoD or to facilitate compliance reporting. To manage these using spreadsheets and manual checks is cumbersome and time-consuming. Audit Manager enables to maintain an SoD model within JD Edwards environment and runs regular checks to identify users with access permissions that might violate your SoD policy. It provides ability to drill down to investigate any SoD conflict issue, and remediate it with accurate information.
View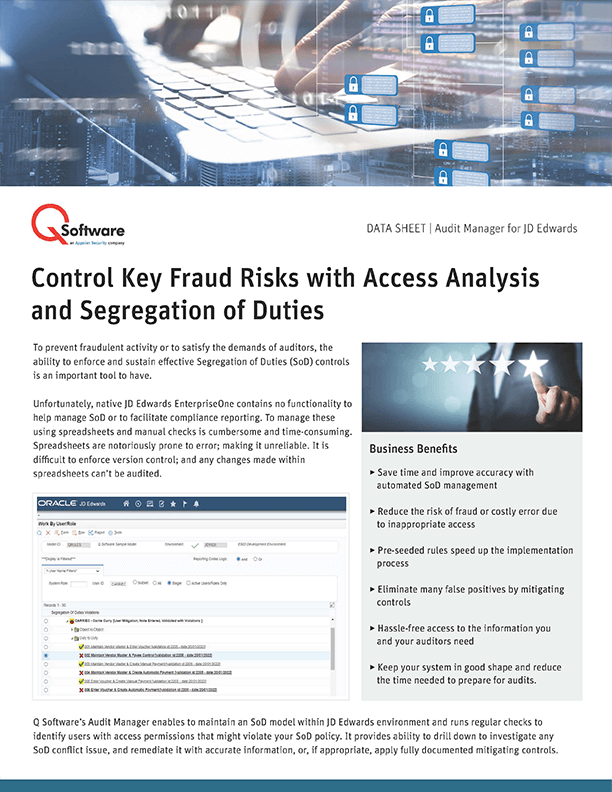
Complexities within the JDE application, deter many organizations from implementing a security tool, which can lead to huge risks and even frauds. QuickTools use a 3-step approach to make it much easier to implement and manage role-based security directly on the F00950 in your JD Edwards, tailored to your needs.
View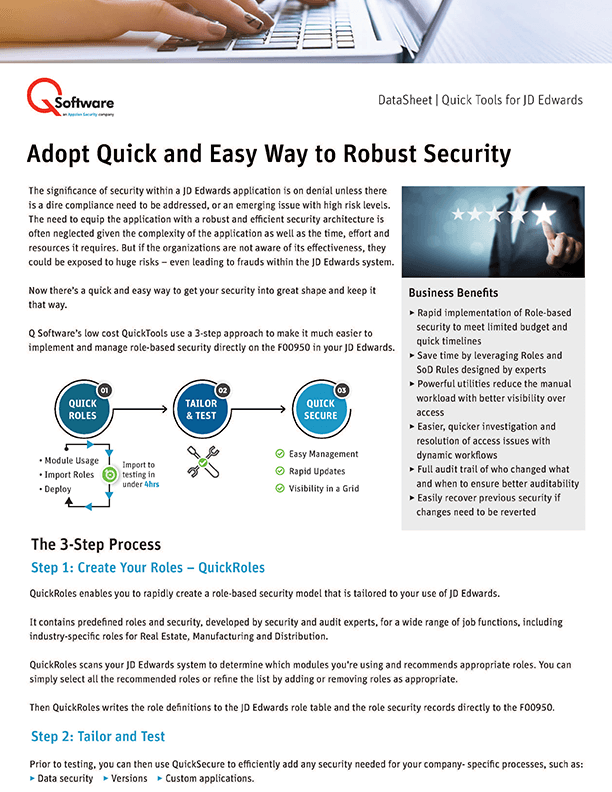
Federal or industry regulations, such as HIPAA or SOX mandate organizations to document, internal controls and processes that adequately manage access to different types of information. User Admin Manager (UAM), provides a configurable workflow to automate the process of requesting, approving and provisioning roles, including proactive Segregation of Duties checks prior to assigning Roles.
View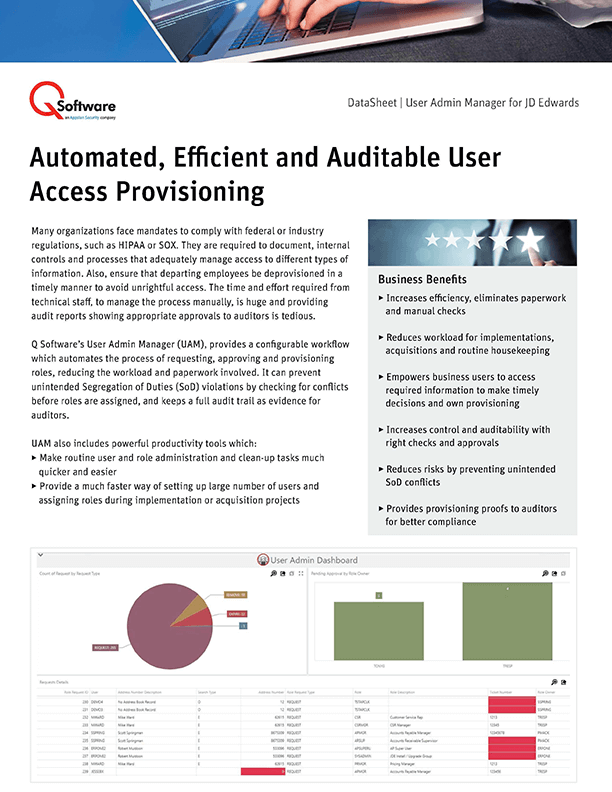
Conducting Periodic Access Reviews can be an extremely painful process, and requires a lot of technical effort to produce access reports. Users find it difficult to wade through reams of unintelligible data to extract meaningful information. With our Periodic Access Review, organizations can automate and simplify the process, and easily produce evidence for auditors.
View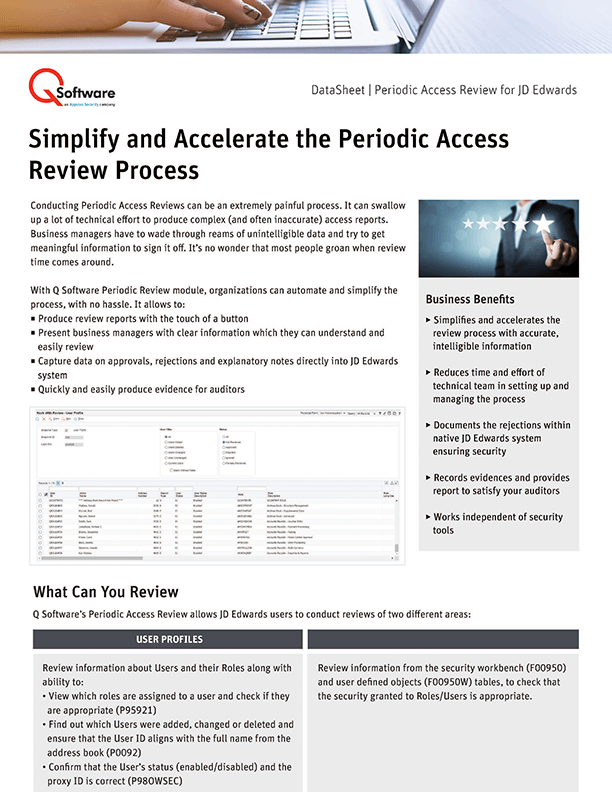
As business grows and changes, it’s important to ensure that your ERP licensing is aligned with current business needs. QCloud License Audit is a Cloud-based service which analyzes user access in your JD Edwards system to identify the licensing requirements and identifies users with redundant access for optimum license utilization.
View
SAP Data Masking is becoming the go-to control to minimize data privacy and security risks without disrupting business processes. While SAP UI Masking is one option, many customers are turning to Appsian’s Dynamic Data Masking for its compatibility in ECC & S/4HANA, rapid scalability, and risk-based enforcement to balance the demands of business and security

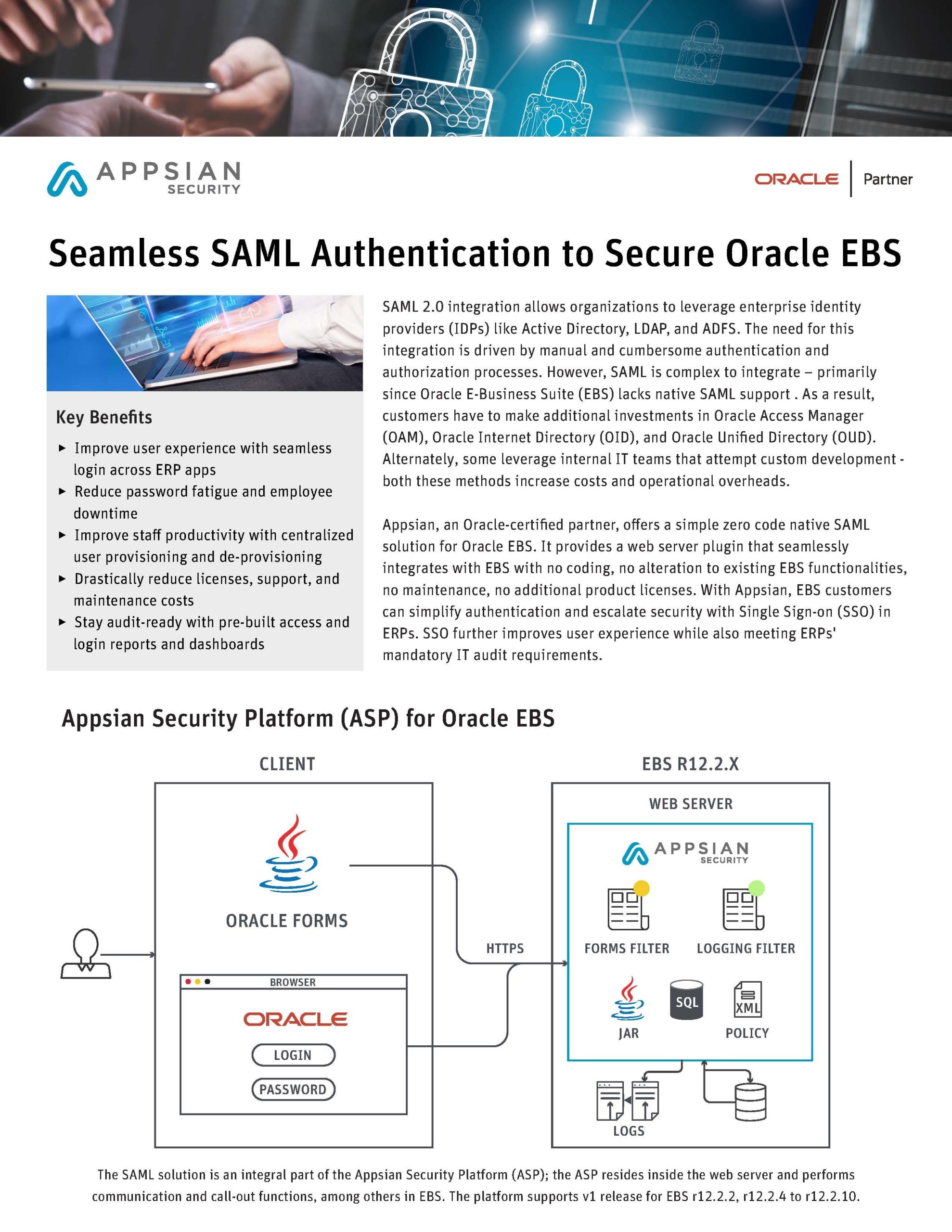
SAML 2.0 integration allows organizations to leverage enterprise identity providers (IDPs) like Active Directory, LDAP, and ADFS. The need for this integration is driven by manual and cumbersome authentication and authorization processes. However, SAML is complex to integrate – primarily since Oracle E-Business Suite (EBS) lacks native SAML support.
ERP applications process and hold customer and employee PII and financial data – high-value targets that need protection from internal and external threats. A vast number of users access your ERP applications from different geolocations, devices, and network connections. The dynamic nature of access makes access governance, data governance, and data security a significant challenge.
Appsian Security’s dynamic SAP data masking capability provides customers with fine-grained control over which sensitive data fields customers can mask for any specified user, in the context of any situation. Unlike other data masking solutions, Appsian Security uses a single ruleset to define and mask data across the entire application.

Gain greater control over user access risks, segregation of duties, compliance, and audit by leveraging cutting-edge technology, machine learning, and predicative analytics continuously identify potential risks and provide optimized suggestions to streamline access management.
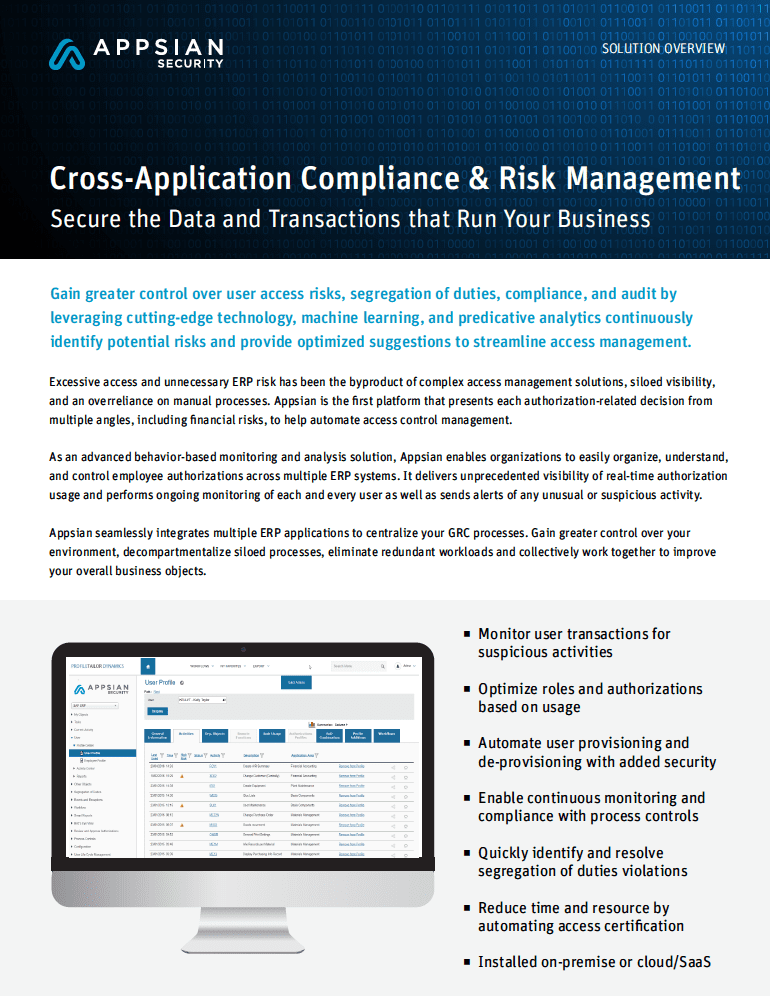
Appsian Security solution includes SoD rules definition, conflict analysis & resolution, real-time violation prevention, and detailed incident analysis. It helps you comply with compliance regulations like Sarbanes-Oxley (SOX) by providing a single control point to manage and enforce segregation of duties (SoD) across multiple ERP platforms.
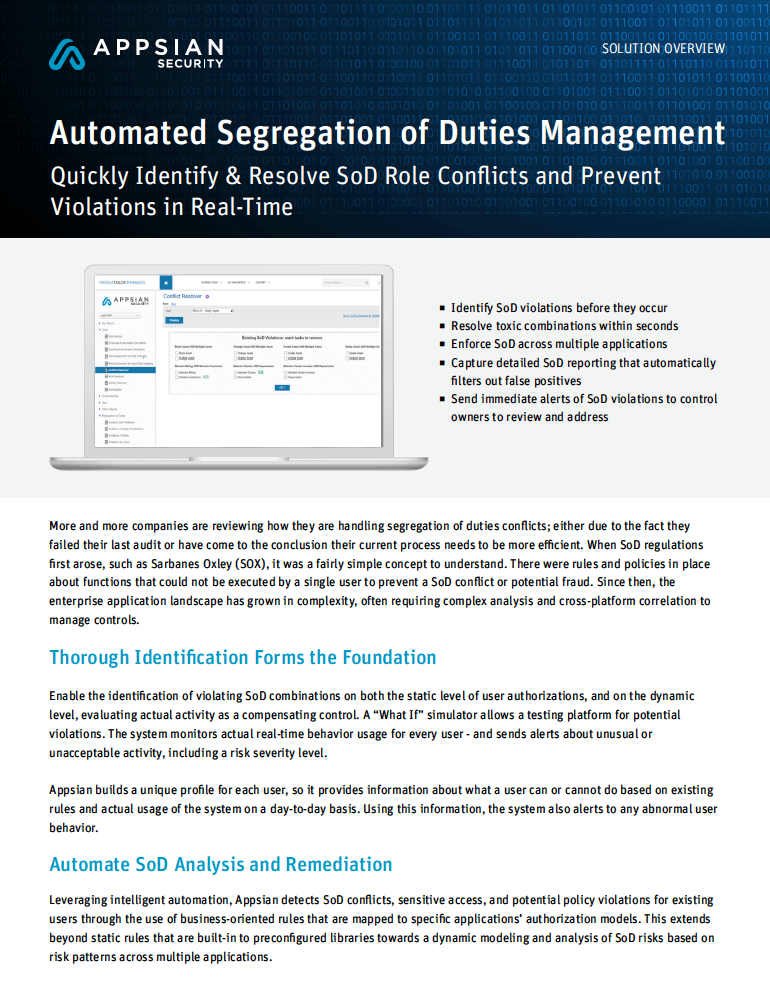
Leveraging advanced behavior-based monitoring and analysis functionality, ProfileTailor GRC enables enterprises to easily organize, understand and control their user authorizations across ERP systems. It delivers unprecedented visibility of actual, real-time authorization usage while performing ongoing monitoring of each SAP user and sends alerts for unusual or unacceptable activity.

While there are several options for selecting a GRC tool, ProfileTailor GRC is one of the most robust solutions available today. Companies can use ProfileTailor GRC as a stand-alone solution or combine it with their existing GRC solution. This guide examines the main differences between ProfileTailor and SAP GRC.
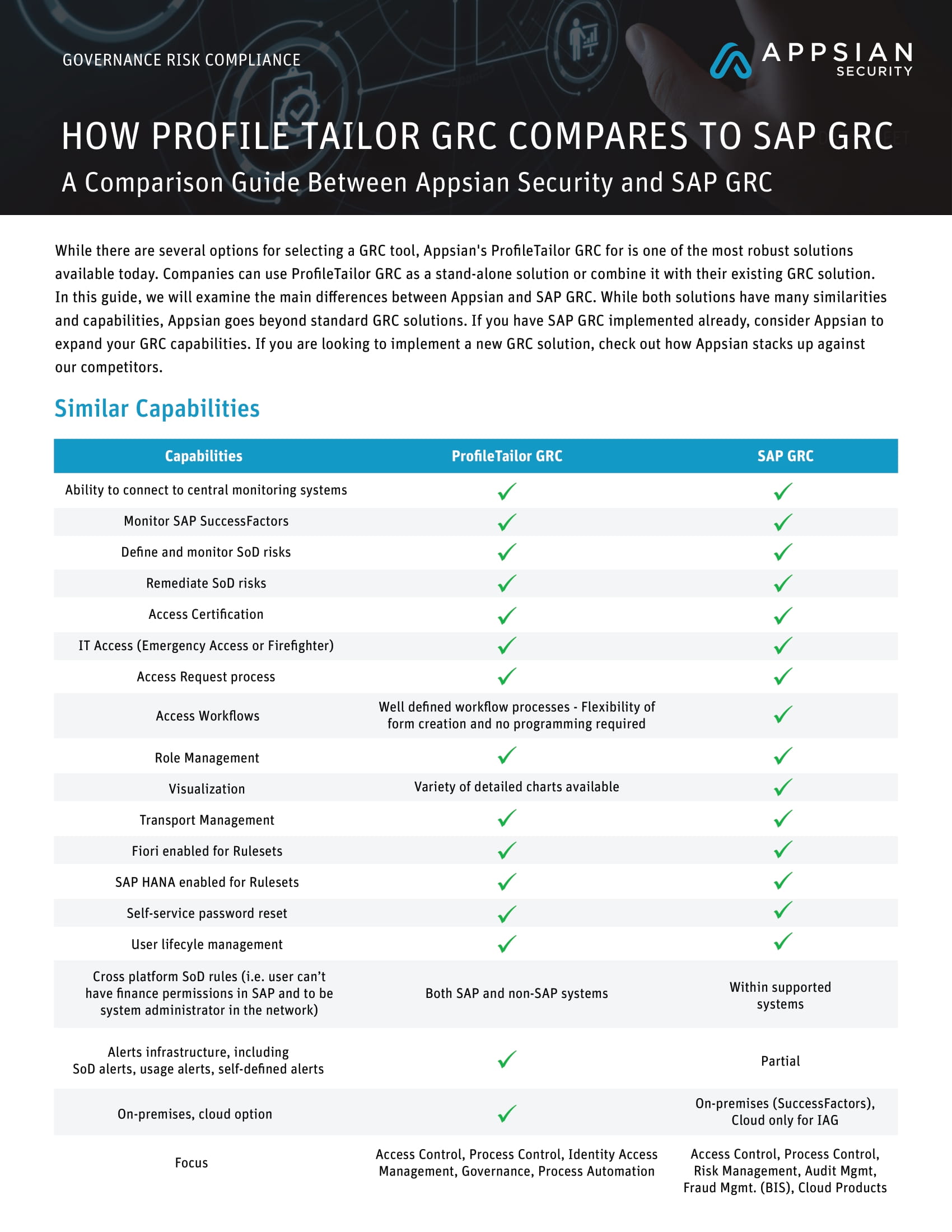
Appsian enhances SAP’s role-based access controls with attribute-based access controls. This approach enables security policies to be dynamic and “data-centric,” leveraging a user’s context of access to determine access to data. Thus, reducing risk. Appsian overcomes the limitations of traditional RBAC, allowing you to fully align SAP security policies with the objectives of your business while streamlining audits and compliance.
View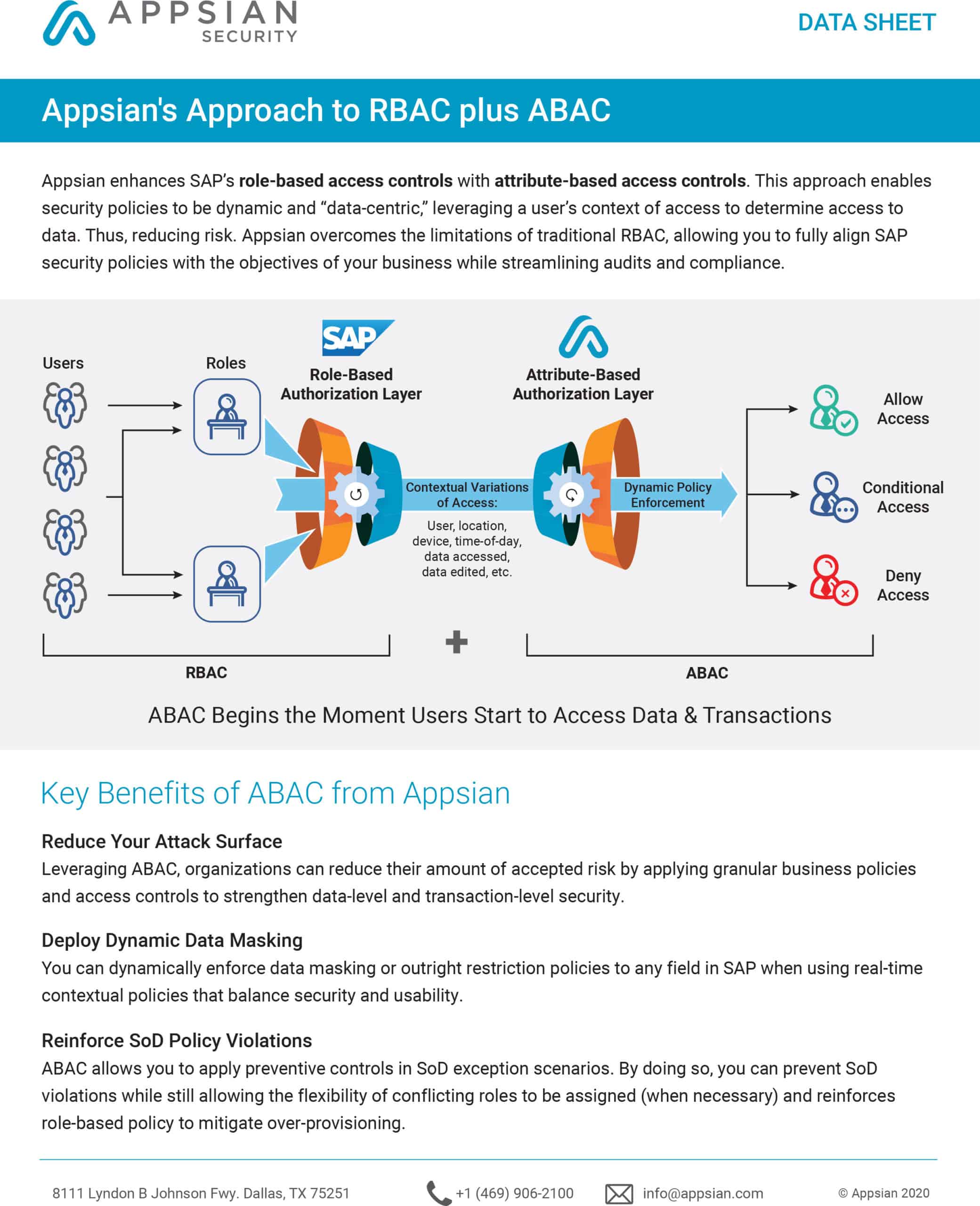
Enable FSCM customers to enhance their authentication strategies while core financial and supply chain transactions are executed remotely
View
Traditional ERP applications like PeopleSoft were designed to provide quick, easy access to data while remaining customizable for any business process. In 2020 the combination of easy access and relying on customizations creates ERP systems that 1) do not enable data security, 2) provide easy access for unauthorized activity, and 3) are unscalable webs of customizations that break with each application update. The status quo has become intolerable.
View
Combining granular insights with enriched processing, Appsian360 provides real-time visibility into the activity around high-risk business transactions. Our visually rich, easily configurable dashboard delivers actionable insight into compliance and business risk along with application utilization and user activity within SAP.

Learn how you can gain detailed insights on all users, locations, devices, and more. Featuring a visually rich, easily configurable dashboard, Appsian360 provides deep, actionable insights that support ERP data security and compliance.
View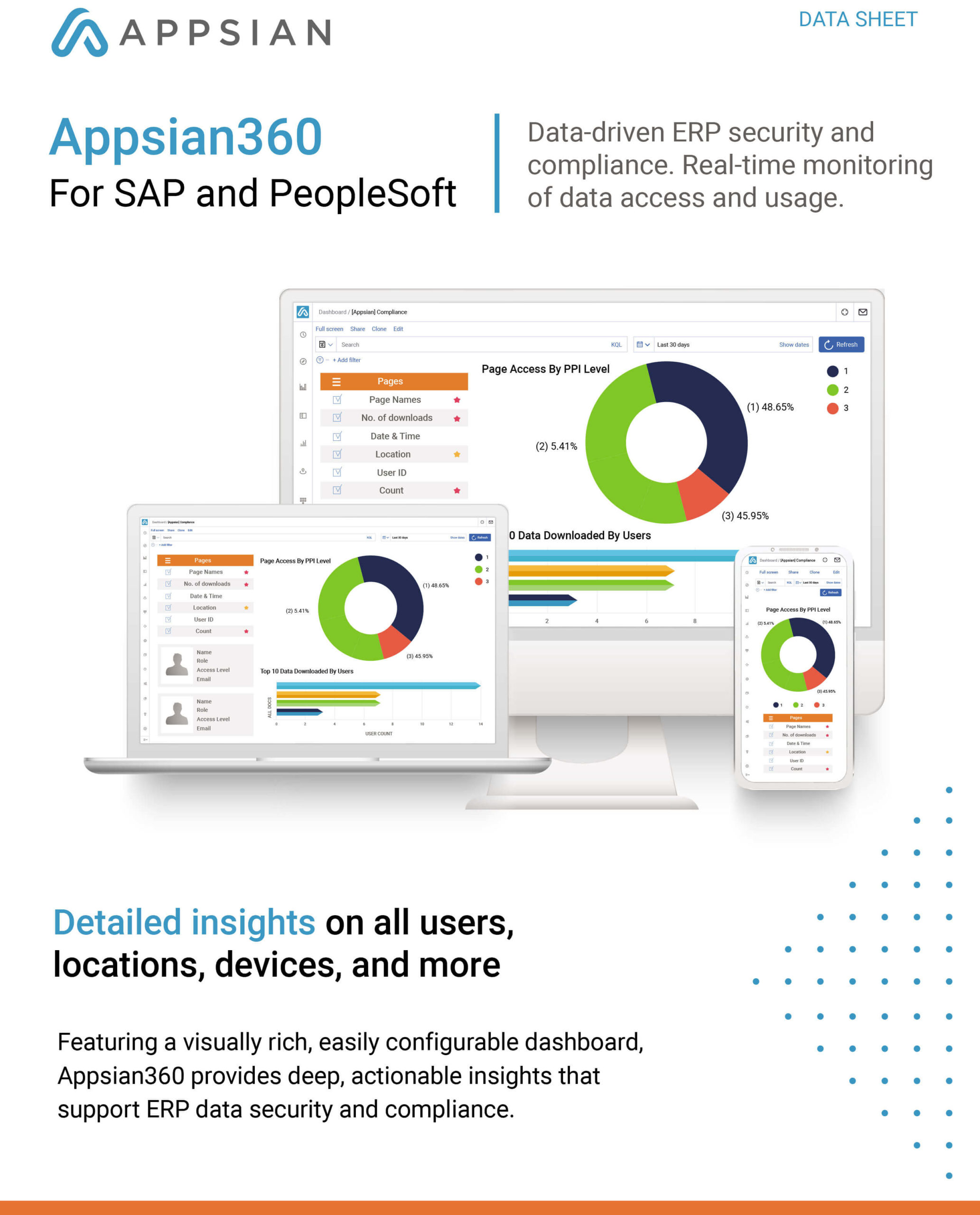
SAML helps pass user authorization between an identity provider and a service provider. Due to PeopleSoft’s lack of native SAML support, most SSO solutions require additional customizations, making them complex and expensive to maintain. Learn how Appsian’s turnkey SSO Integrator can alleviate these challenges
View
SAP GRC Access Control identifies and prevents access and authorization risks by ensuring that the right access is given to the right people based on an employee’s role. Unfortunately, these roles are static, meaning they do not leverage contextual attributes common in today’s dynamic workplace. They require manual updates as users move around the organization and change their job scope.
View
When organizations enable remote access, they need to ensure their data remains secure, yet accessible under the right circumstances.
View
When enabling remote access, high privilege user accounts become vulnerable to security risks. Tracking these accounts should be a business objective for all organizations.
View
Enabling mobile access to PeopleSoft is a primary objective for many organizations. Naturally, there are security concerns when making transactions available on the internet.
View
Combine Contextual DLP Policies with Dynamic Data Masking for Fine-Grained Control Over Sensitive Data Exposure
View
Appsian provides comprehensive security with protection at the Application, Transaction and Data layer. In a single platform, Appsian helps protect user identity with zero trust at the application layer, prevent role-level (segregation of duties) conflicts at the transaction layer, and protect PII at the UI (data) layer. All while delivering real-time security analytics that provides deep visibility into data access and usage.
Appsian enables SAP customers to effectively address the risks associated with ERP business transactions. By adding sophisticated controls that strengthen access policies and enhance logging & analytics capabilities – unauthorized activities that lead to fraud…
View
Compliance mandates like SOX, GDPR, CCPA and others require organizations to maintain details of data access. This information is currently not available out-of-the-box and leaves organizations exposed to compliance risks. Appsian’s Compliance Risk Analytics dashboard equips SAP customers with direct, real-time visibility into the activity around high-risk business transactions. Data access is logged and visualized in-service to rapid threat detection and response.
View
Learn how Appsian integrates native SAML functionality in PeopleSoft to deliver a seamless Single Sign-On. Incorporate PeopleSoft into your enterprise IAM for maximum productivity and security
View
Challenges frequently come up in the testing phases on a PeopleSoft Single Sign-On project. This is typically because organizations fail to address a few inherent issues that make an SSO for PeopleSoft successful. In this data sheet, we’ll give you the 6 questions that will help you avoid a failed SSO project
View
Multi-Factor Authentication (MFA) has become essential for strengthening the security posture for PeopleSoft. However, integrating a 3rd party MFA can present challenges. As a work-around, many organizations scope extensive customizations that delay project completion and interfere with future PeopleSoft application updates. Also, these custom projects force the implementation of arbitrary rules that commonly lead to user friction due to ‘over-challenging’ during routine, low-risk transactions.
View
Next-generation software for monitoring how your PeopleSoft data is accessed. By whom, how, and where.
View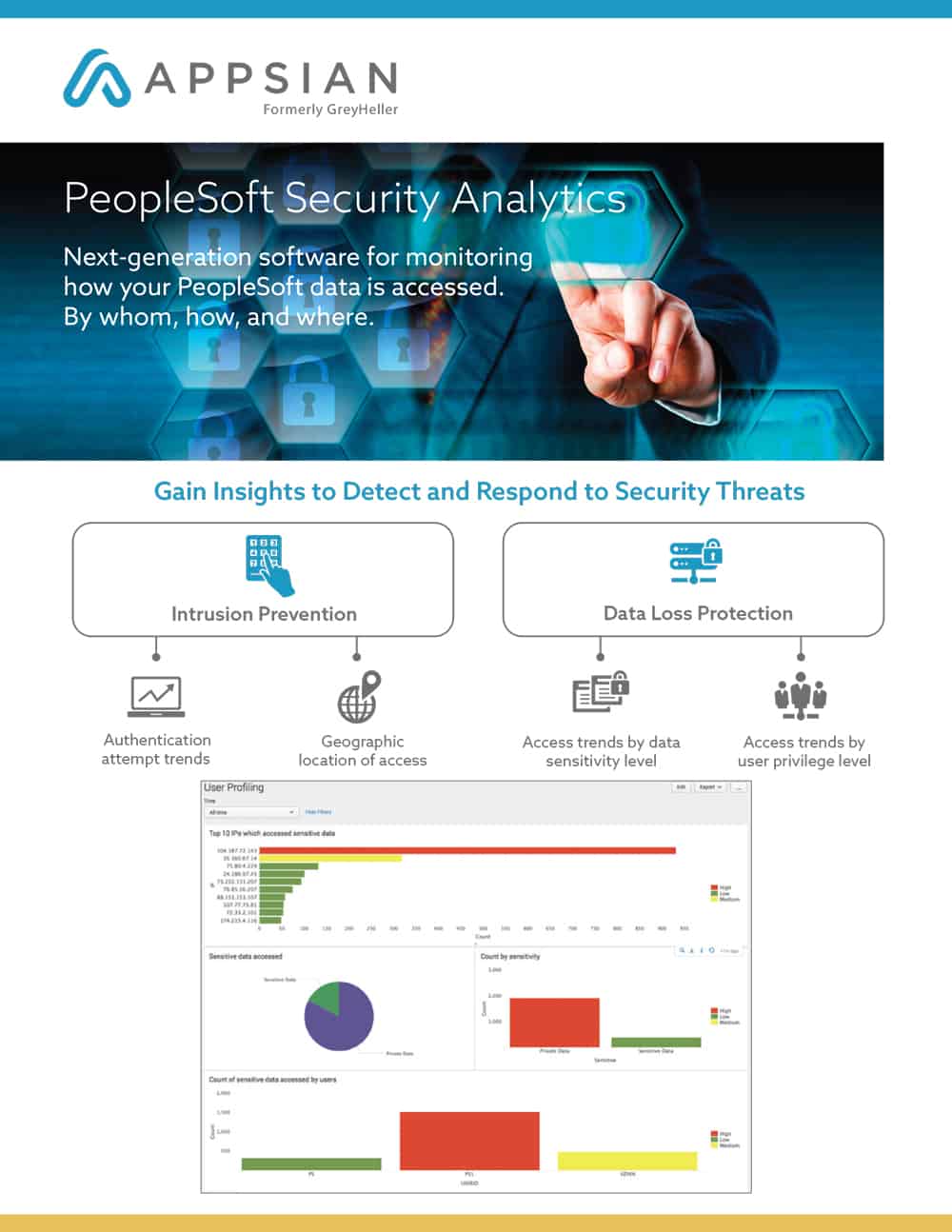
Prevent data leakage from both privileged accounts and normal end-users by ensuring data can only leave SAP in secure environments.
View

"Learn how you can reduce risk with rapid threat protection, audit response and access control. All from a single, comprehensive platform"
Trusted by hundreds of leading brands





