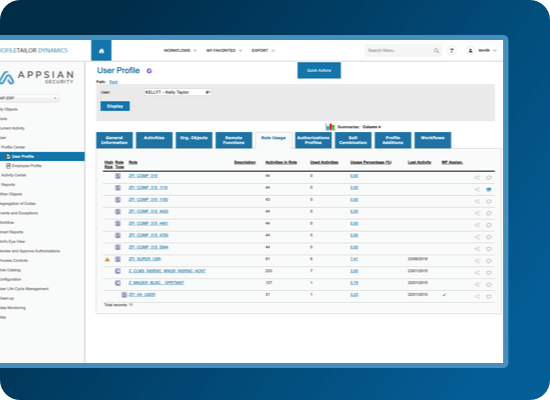
- The Appsian provisioning feature was designed with both novice users and professional experts in mind. Novice users can quickly feel like experts, having all the in-depth data of authorizations without the need to delve into the details. You can optimize authorization roles and be in control over sensitive permissions without needing high-end technical knowledge.
Internal controls experts can enjoy a simple yet intense analytics tool that can help them investigate and improve the current authorization situation. Many experts have proclaimed it the easiest and best analytical tool to deeply investigate authorizations and get insights that they couldn’t have gained elsewhere.