Legacy ERP Logging Doesn’t Meet the Demands of Modern Security and Compliance Requirements
With the expansion of remote access, the shift to user-centric threats, and the growing number of data privacy and regulatory mandates, organizations using legacy ERP systems are facing a visibility gap related to understanding granular levels of ERP data access & usage. This lack of visibility exposes organizations to a myriad of data security and compliance threats like hacking and phishing, along with fraud and theft from internal users. All of which result in the loss of millions of dollars each year.
Understanding details around ERP data access and usage is critical for maintaining strong security and compliance audit strategies. However, legacy ERP logging features were designed primarily for debugging and troubleshooting and lack the capabilities necessary for today’s modernized security and compliance audit requirements.
Organizations all around the world are facing a growing number of data privacy mandates that require direct visibility into how companies store, use, and process personally identifiable information (PII) and other sensitive data. Unfortunately, ERP security and compliance audits are time-consuming, manual processes that are often done at irregular intervals, leaving organizations exposed to risk.

Limitations of Traditional ERP Security & Compliance Audit Response
- Legacy ERP logs were designed for troubleshooting, not granular activity logging that provides detailed information on who is accessing what data, when, and from where on which devices.
- Organizations must sort through network/firewall activity manually to locate anomalies in transaction logs that indicate unusual activity and can be tied to changes in the database.
- Auditing access and update activity requires extensive customization.
- Fully leveraging native logging features can have a negative impact on system performance.
- Without a complete audit trail of user activity to identify or investigate a breach accurately, security teams are often required to make assumption-based decisions.
- Manually analyzing network and database logs delays incident response times.
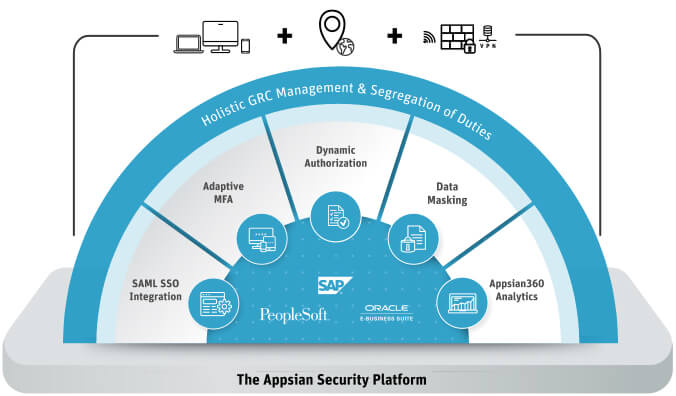
Appsian Provides ERP Defense in Depth A Comprehensive Platform for Adaptive Risk Management
Vulnerability Scanning
* Assess & validate the security of ERP applications
* Uncover vulnerabilities that lead to external & internal risks
User Authentication
* Natively integrate enterprise IAM solutions like SSO & MFA
* Re-authenticate users during sensitive transactions
Access Control
* Dynamic authorization for high privilege user
* Restrict access to data with fine-grained controls
User Behavior Monitoring
* Log & Capture granular user activity
* Aggregate & Visualize activity data for actionable insights

Establish Stronger Compliance and Rapid Incident Response Strategies
-
Avoid Unnecessary Data Exposure with Dynamic Access Controls
Control the resources users access, how they access them, and from where they access them by leveraging the contextual attributes of access such as geolocation, time of day, and IP address.
-
Enable Rapid Threat Detection & Incident Response Times
Gain insight into privileged account behavior and streamline investigations with detailed incident reports for a rapid and thorough response.
-
Perform Forensic Investigations with Context
Drill into granular incident details to gain actionable insights into what was accessed and by whom.
Unique Benefits
-

Maximize Your ERP Investment
Modernize legacy applications to meet current business requirements
-
Modernize Risk Management
Enable risk management with greater control and visibility over data access
-

Extend Access Beyond the Firewall
Provide secure, remote access to users using dynamic & fine-grained authentication, authorization & visibility
-

Lightweight & Quick-to-Deploy Solutions
Natively integrated into ERP web server without requiring customizations or additional servers