How Do Phishing Attacks Impact ERP?
Latest studies indicate that up to ‘81% of successful hacking attacks involve a stolen user credential.’ This means that it’s no longer a question of ‘if’ a user’s credentials could be exploited, but ‘when.’
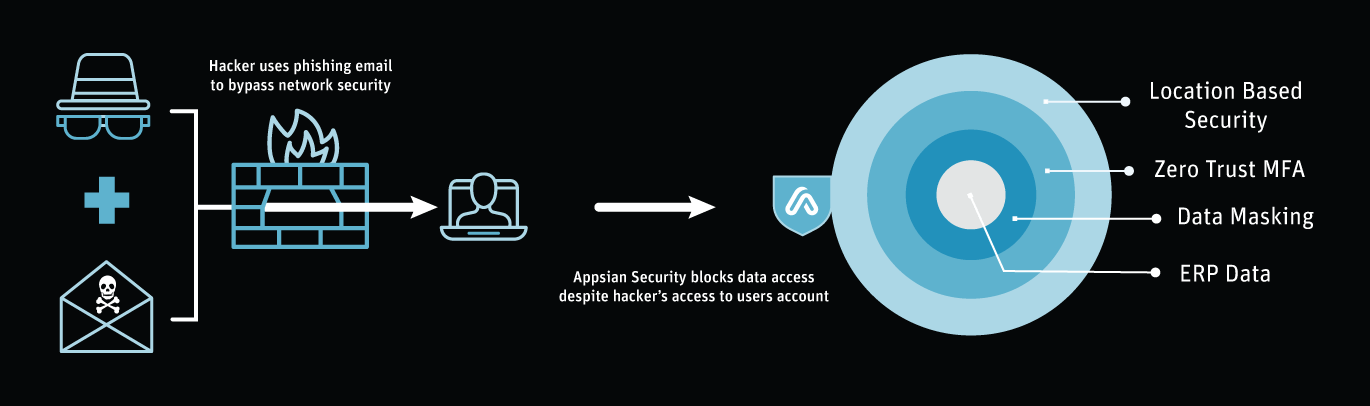
ERP applications like PeopleSoft, SAP, and Oracle EBS primarily rely on the username/password security model, leaving data vulnerable if a user’s credentials get into the wrong hands. Traditional security/governance features like VPN and role-based access controls are not intended to secure data – rather application access. Implementing an authentication strategy that enables data security is the most effective protection against a successful phishing attack.
Appsian Security provides the necessary security layers (below your network and application controls) to protect data, even if a hacker is already inside your application. The Appsian Security Platform uses a combination of zero trust IAM, attribute-based access controls and real-time analytics for effecient phishing prevention and to help you keep your data out of the wrong hands.
Request a Demo
See how we can help you secure your ERP Data with our phishing prevention solution.
Key Features
Integrate enterprise IAM (SSO & MFA) at multiple layers of the ERP application to enable zero trust authentication.
Integrate with your SAML identity provider to ensure your ERP is included in your enterprise identity management strategy.
Be alerted to suspicious activity including access from foreign countries, account number changes, report/query downloads, and more.
Automate critical internal audits with granular, real-time data access and usage information.