MFA Is A “Critical Security Baseline” for Your Zero Trust Strategy
Following up on last year’s Executive Order to help improve the nation’s cybersecurity posture, the White House released a 30-page zero trust strategy document outlining several measures federal agencies must enact to secure systems and limits the risk of security incidents.
The White House noted that the growing threat of sophisticated cyberattacks (for example, SolarWinds, ransomware, and Log4j vulnerability) underscores that the Federal Government “can no longer depend on conventional perimeter-based defenses to protect critical systems and data.”
And neither should you.
Instead, the Federal Government will focus on multifactor authentication as a critical part of its security baseline. In fact, strong authentication, as provided by a strong and dynamic MFA, is a necessary component of any zero trust strategy.
What’s Good for the Feds is Good for the States
If you’re a state or local government, I recommend that you review the White House’s zero trust strategy document. You won’t be bound by their mandated timelines, but the document is full of best practices and sound advice. Briefly, the security goals are based on the maturity model developed by the Cybersecurity and Infrastructure Security Agency. CISA’s zero trust model describes five complementary areas of effort (Image Source: White House):
Again, all good advice. I want to point out two key actions mandated by CISA related to multifactor authentication:
- Federal Agencies “must employ centralized identity management systems for agency users that can be integrated into applications and common platforms.”
- MFA must be enforced at the application layer instead of the network layer.
Unfortunately, the majority of our clients in the government sector use ERP applications like PeopleSoft, SAP ECC, and Oracle EBS whose native architecture does not allow for the seamless integration of MFA solutions that can be A) integrated at the field/transaction levels of workflows or B) deployed dynamically with each unique context of access.
These traditional ERP applications use static security controls to govern access. These controls fail to provide protection beyond the traditional perimeter-based security because they do not leverage contextual attributes. Put another way, these ERP systems do not allow a seamless integration of MFA solutions and make it challenging to achieve strong authentication for zero trust.
Centrally Managed MFA to Enable Zero Trust Security with Appsian
Fortunately, requiring dynamic MFA that is integrated inside ERP applications is one of the most common use cases our Appsian Security Platform solves.
The platform can enforce zero trust security policies that can dynamically secure data and regulate access based on contextual attributes (e.g., IP address, time of day, location, user security clearance, data classification, device used, max dollar amounts, etc.). Additionally, Appsian can help bring your zero trust strategy to life with:
- Context-Aware Access Controls (with ABAC) – Fine-grained controls help you set dynamic access permissions for users down to the transaction and field level
- Step-Up Authentication – Integrate enterprise MFA at field level for re-authentication when a user requests access to sensitive data
- Transaction Monitoring & Control – Monitor high-risk transactions and automatically remove privileged access rights to stop potentially high-risk user activity
- Data Masking – Enforce full, partial, or click-to-view data masking to obscure sensitive data and protect against unnecessary data exposure
- Logging & Analytics – Capture detailed logs to get real-time visibility and insights into user access, IP address of frequent transactions, asset inventory, and other vital data.
Contact Appsian today for a demo to learn how we develop native integrations between Oracle and SAP ERP applications and some of the top MFA providers in the market.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
6 Warning Signs Of Potential Insider Threat Activity And How To Detect Them
Data breaches caused by ransomware attacks, phishing scams, and state-sponsored hacker groups tend to grab the headlines. However, the reality is that insider threat activity causes 60% of these breaches. Moreover, while these threats are becoming more frequent – up 47% over the latest two-year period – and costly to organizations, it still takes organizations more than two months to discover and contain the average insider threat incident (an average of 77 days). And the longer an insider incident lingers, the more costly it becomes.
Why Insider Threat Activity is Difficult to Discover
A primary reason for the lengthy discovery time is that it is difficult to distinguish between regular user activity and the kind of user behavior indicating an insider attack. Complicating discovery further is that the insider in question usually has authorized access to the ERP system and knows how to bypass controls and violate security policies.
How can a company become more proactive at detecting insider threat activity rather than waiting (up to 77 days) to discover that an incident occurred? One solution is to continuously monitor user activity around data access and usage inside the ERP.
What are Potential Insider Threat Indicators?
When companies monitor for outlier and abnormal behavior patterns, they are more likely to detect possible malicious activities or compromised accounts, reducing the discovery and containment time and costs. Here are six user behaviors to monitor that could indicate potential insider threat activity.
1. Making Unauthorized Changes To Master Data
The exponential growth in data volume and usage in companies has led to storing sensitive master across multiple siloes. Any changes to master data, such as changes to payroll or adjusting a PO amount beyond limits, are worth paying attention to as possible indicators of insider threat activity. It is critical to know precisely who is accessing master data and how frequently.
2. Unusual Login Times And Off-Peak Activities
Watch out for users trying to log in outside of their regular working hours without proper authorization or a valid need to access the network at odd hours or from an unknown IP address. Of course, there could be a legitimate reason for this access, but this behavior is worth investigating. For example, does the employee genuinely need to access payroll information outside of office hours?
3. Repeated Failed Attempts At Logging Into Critical Applications
Organizations typically have a fixed set of users and roles that have access to sensitive data. Repeated failed attempts to access data, or complete transactions could be a warning sign that an insider is trying to access privileged information (e.g., PII, compensation data of others).
4. Erratic Behavior Of Privileged Accounts
Privileged users in companies have elevated access to sensitive data and transactions. Watch out for these users accessing particularly sensitive fields, including compensation data and executive payroll, and how frequently. These behaviors are usually a violation of a company’s security policies and protocols and can indicate behavior with malicious intent.
5. Questionable Query Running and Data Downloads
A key indicator of insider threat activity is running queries and downloading sensitive data to unauthorized devices. Companies should monitor instances of query running and download attempts of sensitive data onto unauthorized devices, from suspicious locations, or outside business hours. Additionally, when employees use unapproved workarounds for transferring potentially sensitive information to cloud storage accounts for easy access, it leaves vulnerable data and resources unsecured and vulnerable to hackers.
6. Unnecessary or Excessive Vendor Creation and PO Approvals
Employees using their credentials to create new vendors, purchase orders, requisitions, etc., are likely engaging in fraudulent activity that leads to data or financial theft. In addition, without proper internal controls in place, employees can use their credentials to violate segregation of duties for financial gain.
Detect and Prevent Insider Threats with Data-Centric Security
An essential first step to tackling insider threats is closely monitoring user behavior around data access and usage. With continuous monitoring, security and compliance leaders can drill into specific activity and know exactly the context of data access and usage: who is doing what, where, and why. With that level of in-depth, contextual information, any red flag incidents can undergo a rapid response plan.
The next step is to prevent insider threat activity by adopting a layered, data-centric security model that includes –
- Enhanced access controls with dynamic authorization policies
- Expanded use of data masking to all fields considered personally identifiable
- Stepped-Up Multi-Factor Authentication to prevent unauthorized access
We have helped several organizations detect and defend against insider threats by applying continuous data access and usage monitoring at a granular level combined with a data-centric security approach. Contact us to chat with an Appsian Security expert today.
Related Reading: These behaviors usually align with one of these five categories of insider threats.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How Enhanced Logging Enables Better Breach Investigation, Remediation, and Security
Every time a major data breach makes the headlines, the company in question almost always struggles to answer the most important question: Why did it take so long to detect the breach, and what exactly did the attackers steal? Even though companies maintain transactions logs, investigators need to look at log entries that could run into the millions to find out what was accessed by whom and when. This affects the investigation, remediation, and calls the company’s data security practices into question.
Connecting the Dots with Multiple Log Files is a Challenge
When asked how the U.S. government missed the SolarWinds and Microsoft Exchange Server hacking for so long, National Security Agency Director Gen. Paul Nakasone said, “It’s not the fact that we can’t connect the dots — we can’t see all the dots.” This is a very significant statement and highlights a serious problem with breach detection and remediation.
Many companies use legacy applications like PeopleSoft or legacy versions of SAP for their business operations. They store vast amounts of sensitive and confidential data that is essential to facilitate day-to-day transactions. However, once the user gains access, these applications offer limited monitoring and logging capabilities – creating blind spots that allow intruders to stay undetected for months.
According to the 2020 IBM Cost of a Data Breach Report, it takes 280 days, that’s more than nine months, to identify and contain a breach. Even with robust monitoring and logging capabilities in place, the volume of raw log information generated makes it virtually impossible to determine any meaningful insights to make a timely impact.
In fact, it is routine for incident detection teams to end up sorting through more false positives than malicious activities that are the real threat. Considering the volume of log data, it is rare for security teams to spot potentially malicious behavior in time to take preventive measures. And should a breach occur, investigation and forensics teams are confronted with a mountain of log entries that need to be analyzed to estimate the damage.
How Logging and Detection can be Enhanced
Logging and monitoring are important security measures that enable both prevention and detection of threats. Logging allows you to understand user behavior, trace malicious activity, and react to incidents enabling faster detection. In the event of a breach, logs allow forensic investigators to reconstruct events, determine the extent of data exposure, and take effective steps to remediate the problems that led to the breach. Here are some of the ways companies can enhance their logging capabilities to detect and prevent threats.
Granular Activity Logging
Most applications offer some degree of monitoring and logging, but security teams need to decide if the recorded log data is granular enough. In many cases, applications provide limited visibility into user activity once access has been granted. Transaction details like what data was accessed, by whom, from where/what device, and why are crucial to determining context and risk. These details enable faster detection and allow administrators to run reports and perform audits.
Access Checkpoints
Users perform multiple transactions and access a variety of data every day, including PII and confidential data. Using dynamic data masking and creating checkpoints like Click-to-View and Step-Up MFA to access specific data fields within your ERP ecosystem ensures that data isn’t needlessly exposed and access to sensitive data is always logged. This also creates an audit trail that aids investigation and remediation efforts.
Real-Time Monitoring
Monitoring and logging are essentially two sides of the same coin for the simple reason that you cannot monitor what you’re not logging. A real-time monitoring and analytics tool that draws insights from the vast volume of logs that are generated every day enables security teams to get detailed information on transactions and data access, failed login attempts, and potential brute force attacks. Such tools also provide administrators and auditors with detailed reports and visually rich dashboards that show trends in behavior and usage.
As attacks increase in frequency and sophistication, companies and government departments are trying to find ways to detect attackers faster and initiate remediation to prevent future attacks. The 2020 SolarWinds attack was a stark reminder of the extent of damage hackers can cause. It even prompted the U.S. President to issue an Executive Order which asks federal departments to strengthen their cybersecurity defenses and improve investigative and remediation capabilities.
While logging is vital for breach investigations and remediation, it can also be used as a tool for proactive and preventative security. By enhancing logging and monitoring capabilities, companies can not only bring down the dwell time but also derive insights that enable active detection and reduce potential security incidents.
Monitoring and Logging with Appsian
Appsian Security enables you to enhance your logging capabilities by capturing granular transaction details within your ERP applications. Controlled by a configurable rules engine, Appsian lets you add click-to-view features to log exposure of specific data fields and enforce step-up authentication for sensitive transactions. Appsian360, a visibility and analytics solution, provides the most powerful, real-time view into your ERP data access and usage while maintaining complete visibility of sensitive business transactions.
Schedule a demo with our ERP security experts to get a first-hand look at our enhanced logging and monitoring solutions.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Unpacking China’s New Data Security Law and Privacy Legal Framework
If you’re a multinational enterprise (MNE) that does business in or with China, you’re likely aware of the Data Security Law (DSL) that went into effect on September 1, 2021. The DSL adds to an increasingly comprehensive legal framework for information and data security in China. The law also imposes extensive data processing requirements and imposes potentially severe penalties for violations.
This article attempts to share a high-level overview of the DSL and put into context the overall state of data governance in China. First, a disclaimer: This article isn’t legal advice. Instead, it is a high-level look at a new set of data governance and regulations that affect our customers. We do recommend that you seek guidance from your legal department and other relevant experts.
A Brief Recap of China’s Recent Data Security Initiatives
The recent legal moves by China over the past few years address the country’s growing concerns over the amount of data collected by firms and whether that information is at risk of misuse and attack, particularly by foreign nations. On June 10, 2021, the Standing Committee of China’s National People’s Congress passed the Data Security Law (DSL), which took effect earlier this month (September). The DSL, together with the 2017 Cybersecurity Law and the just-passed Personal Information Protection Law (PIPL), will form an increasingly comprehensive legal framework for information and data security in China.
Data Security Law Highlights
The primary purpose of the DSL is to regulate “data activities,” safeguard data security, promote data development and usage, and protect individuals and entities’ legitimate rights and interests. Additionally, the DSL focuses on safeguarding China’s state sovereignty, state security, and development interests.
Extraterritorial Jurisdiction
The DSL provides broad extraterritorial jurisdiction. According to Article 2, the law governs data activities conducted within China as well as those outside the country that may “harm the national security or public interests of the PRC, or the legitimate rights of Chinese citizens or entities.”
Defining and Classifying Data
The DSL requires all companies in China to classify the data they handle into several categories and governs how that data is stored and transferred to other parties. The classification system will control data according to the data’s importance (i.e., “important data”) to China’s economy, national security, and public and private interests.
The DSL further introduces a separate regulatory framework for “core state data,” broadly defined as data involving national security, lifelines of the national economy, importance to people’s livelihood, and significant public interests. Core data are subject to stricter processing regulations.
Currently, the data classification system details are not specified in the DSL but are expected to be rolled out in the future.
Data Security Compliance Obligations
The DSL imposes general obligations on companies and individuals who carry out any data activities, including:
- Establishing comprehensive data security management systems, organizing data security education, and implementing necessary measures to ensure data security
- Strengthening risk monitoring, taking corrective actions when data security flaws or “loopholes” are discovered, and notifying users and authorities of security incidents
- Conducting regular risk evaluations of the data activities for “important data” processors and reporting results to relevant authorities.
The more sensitive the data a company handles, the more rigorous the data security obligations. For example, in addition to obeying strict processing restrictions for “national core” data, entities that process “important data” must:
- assign a data security officer,
- create a data security management department,
- conduct regular evaluations to monitor potential risks, and
- report results to appropriate government agencies.
Cross-Border Data Transfer Requirements
There are many details about cross-border data transfers that we won’t cover in this article. But, basically, the DSL doesn’t allow the transfer of any data from China to any foreign law enforcement agencies or judicial bodies without approval from the appropriate Chinese government authorities, creating complications for companies legally required to submit data to foreign authorities.
For example, companies established in China that offer goods or services in the European Union (EU) are subject to the EU General Data Protection Regulation (GDPR), which allows EU supervisory officials to request data when exercising their enforcement powers. However, China requires that companies receive government approval before transferring data in response to GDPR enforcement requests.
Again, the DSL currently provides no specific guidance to companies on this requirement.
Penalties for Noncompliance
Failure to comply with DSL requirements includes demands for rectification, warnings, monetary fines, forfeiture of illegal gains, revocation of business licenses, and/or orders to close down businesses. Noncompliance with the DSL that scales to a criminal or administrative offense level may also be prosecuted criminally under China’s Criminal Law or be subject to administrative penalties. In addition, the DSL allows parties to recover damages through civil litigation in court.
What’s Next? Here’s How Appsian Security Can Help
MNEs currently conducting business in and with China are likely already used to stingy information and data security controls and may have existing internal policies for information technology, data management, and privacy already in place. Even so, those companies will benefit from additional reviews of their data processing policies and activities for potential non-compliance risks.
Additionally, it’s a good time to talk with Appsian Security to learn how the Appsian Security Platform (ASP) can help you comply with China’s DSL, along with other global compliance regulations like GDPR. ASP gives you complete control and visibility over your business data using a comprehensive platform that combines data security, identity and access management, and governance, risk, and compliance (GRC).
Contact us today for a demonstration.
Sources, references, and further reading:
- “China’s New Data Security Law: What to Know,” by Hui Xu & Kieran Donovan, Latham & Watkins, LLP
- “China Adopts New Data Security Law,” by Colin Zick, Foley Hoag LLP
- “Cross-Border Data Transfer and Data Localization Requirements in China,” by Andrea Tang, CIPP/E, CIPM, ISO27001 LA
- “Translation: Data Security Law of the People’s Republic of China” – Stanford’s DigiChina Cyber Policy Center
- “Unpacking China’s game-changing data law,” by Shen Lu, Protocol
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Data Loss Prevention: 7 Best Practices for SAP Security
A constantly evolving threat landscape and compliance environment with inconsistent standards have made data loss prevention (DLP) a vital component of an organization’s SAP data security strategy. The global cost of data breaches hit a record-high in 2021 ($4.2 million per incident), highlighting the importance of a robust DLP strategy to protect organizations from financial, legal, and reputational damages.
What Is Data Loss Prevention?
Data Loss Prevention is the practice of identifying and preventing data breaches, exfiltration, or unwanted loss or destruction of sensitive data. Businesses use DLP solutions for SAP and PeopleSoft applications mainly to:
- Secure Personally Identifiable Information (PII)
- Comply with data security and privacy regulations
- Protect intellectual property critical to the organization
- Prevent unauthorized transfer of data outside the organization
Seven Data Loss Prevention Best Practices
For any DLP strategy, you need to understand which organizational data to secure, where that data resides, who has access to that data (and when), and how the data should be used. Unfortunately, data loss is difficult to spot because data routinely moves in and out of an enterprise and closely resembles normal traffic. Let’s take a look at a list of data loss prevention best practices that have helped our customers achieve their data security goals and meet compliance standards.
- Configure Dynamic Data Loss Prevention Policies
Preventing unauthorized exposure of sensitive information and protecting against insider data leakage begins by configuring contextual, attribute-based DLP policies that restrict transactions based on user and data attributes. Unfortunately, traditional role-based access controls (RBAC) can’t completely safeguard data in dynamic environments as static roles fail to leverage contextual attributes such as time of the day, geolocations, IP address, transaction type, etc.
- Establish Clearly Defined Rulesets for Segregation of Duties
Establishing a clearly defined ruleset for segregation of duties that divides business processes between multiple users helps limit the risk of fraud and error while ensuring that a user’s access privileges do not conflict or violate business policies.
- Deploy Policy-Based Data Masking and Redaction
Companies can enable dynamic data masking to reduce unnecessary exposure of sensitive information while allowing employees to do their jobs. For example, masking specific fields on a page an employee is accessing. Or using click-to-view masking to unmask data or require an MFA challenge before data is revealed to log access to a particular field. And don’t forget to protect non-production environments where dynamic data masking ensures development or testing teams can only access the data they need and nothing more.
- Continuously Monitor Data Access And Usage
Monitoring user behavior around data access and usage in real-time at a granular level provides visibility into how users interact with sensitive data, triggering security event alerts for high-risk access and abnormal activity at the field level. (Native application logging capabilities cannot tell the difference between malicious user activity and normal usage.)
- Increase The Levels Of Access Control & Monitoring for High-Privilege Users
Because privileged user accounts are magnets for hackers, companies should isolate activity and access data by these accounts to ensure integrity and alignment with current business policies. For example, an employee from the HR department needs access to payroll information to do their job, but do they need that access outside of office hours or from an unknown IP address?
- Closely Monitor Report and Query Downloads
Monitor instances of query running and download attempts, ensuring that sensitive queries are not being downloaded onto unauthorized devices, from suspicious locations, or outside business hours.
- Leverage DLP Solutions to Automate As Much As Possible
For all the features and value ERP systems provide, they lack the functionality to provide a dynamic, automated data loss prevention solution. Automating DLP processes across the organization allows you to enforce dynamic policies to identify and protect data before it exits the organization. In addition, automating compliance audits allows you to constantly monitor data access and usage and alert security teams to abnormal activities.
How Appsian Security Helps Enable Your SAP Data Loss Prevention Strategy
Whether careless or malicious, employee, partner, or contractor, it can be difficult to tell the difference between a user’s regular activity and activity intent on causing harm or theft. The Appsian Security Platform (ASP) helps SAP customers deploy these data loss prevention best practices, and many more, to prevent unauthorized exposure and exfiltration of sensitive data, PII, and intellectual property.
By configuring dynamic access controls, you can uniformly enforce policies that restrict transactions based on user and data attributes. In addition, you can deploy policy-based data masking that help you comply with data security and privacy regulations by reducing the exposure of high-risk data.
Contact us today for a demonstration and see for yourself how Appsian Security can help with your data loss prevention strategy.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How to Protect Your ERP With an Adaptive Security Model
Agility is the name of the game in today’s ERP data security landscape. Organizations are being challenged to detect threats as they happen, quickly address vulnerabilities, and continuously improve their security posture while protecting crucial ERP data as well as their overall business. One strategy that is helping organizations become more proactive is aligning to an adaptive security model.
Focused on operationalizing agile, context-aware, and adaptive technologies, an adaptive security model enables organizations to strengthen security and leverage automation for continuous improvement.
What is Adaptive Security?
Adaptive security is an approach to managing security that analyzes behaviors and events to protect against and adapt to threats before they happen. With an adaptive security architecture, an organization can continuously assess risk and control effectiveness monitoring and automatically provide proportional enforcement that can be dialed up or down to fit its need.
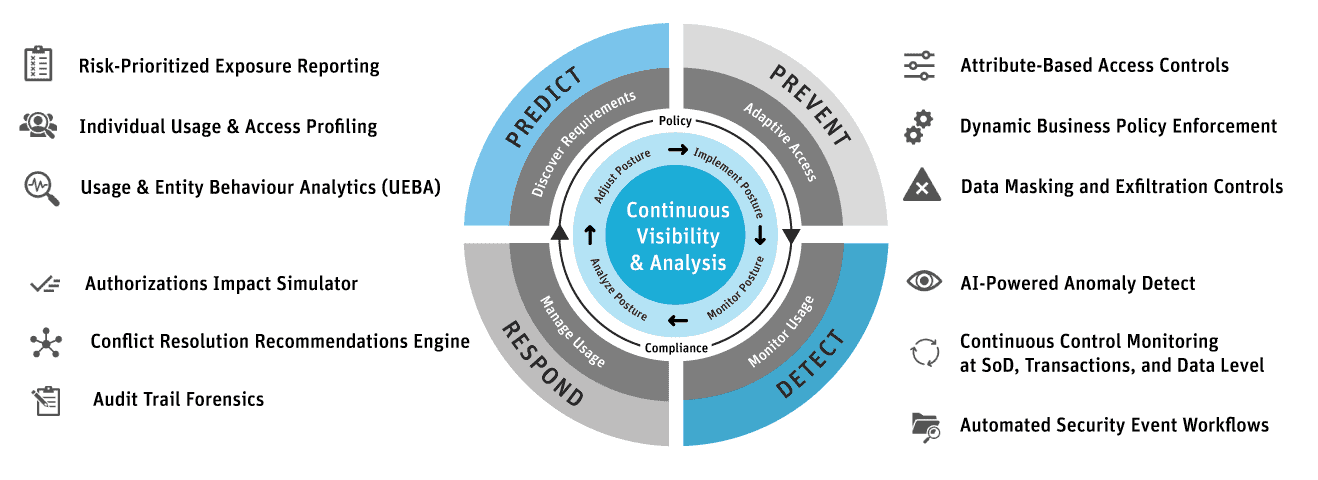
Figure 1: Adaptive Security Architecture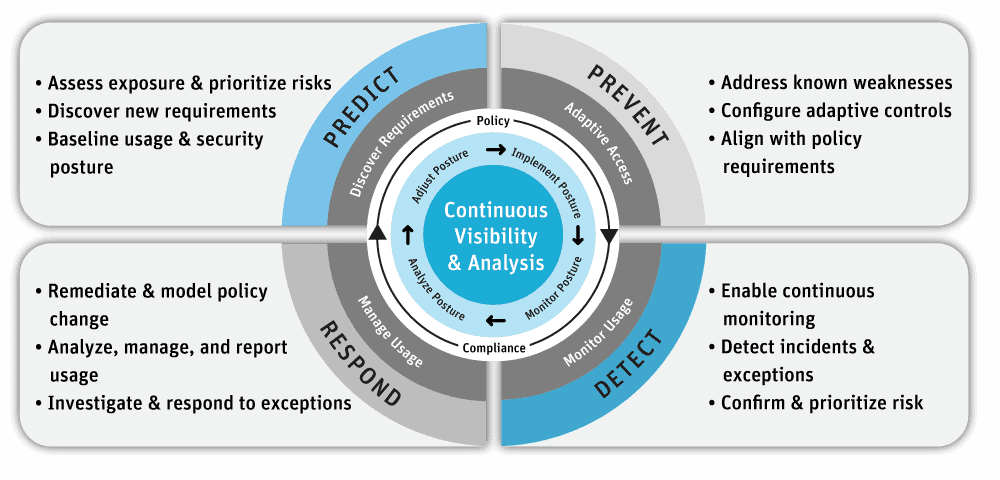
You’ll note that there are four stages of an adaptive security architecture: Prevent, Detect, Respond and Predict. These stages help organizations transform the old static, roles-based approach to ERP data security to a continuous monitoring and risk-adaptive approach. Zero trust is a core concept to adaptive security, which promotes continuous monitoring and analysis as a starting point, enables rapid detection of behavioral anomalies, and permits rapid responses to quickly stop and resolve security incidents.
Seven Imperatives for an Adaptive Security Architecture
According to Gartner, supporting digital business transformation in an environment of advanced threats requires a new approach for all facets of security. Security and risk management leaders can use these seven imperatives of an adaptive security model to embrace the opportunities and manage digital business risks. Each imperative is Gartner’s recommended capability required of your ERP security, risk & compliance solution to enable the security model.
- Replace One-Time Security Gates with Context-Aware, Adaptive, and Programmable Security Platforms
Organizations need to replace the initial one-time, yes/no risk-based decision at the main gate to their systems (typically managed by a static authentication and authorization process) with a continuous, real-time, adaptive risk and trust analysis of user anomalies with context-aware information across the platform. Context-aware security (also known as attribute-based access controls or ABAC) uses situational information, such as identity, geolocation, time of day, or type of endpoint device. - Continuously Discover, Monitor, Assess and Prioritize Risk — Proactively and Reactively
Risks events are fluid and require constant identification, analysis, prioritization, monitoring, and response after the initial login assessment. This should include a combination of proactive and reactive capabilities. For example, if a user attempts to download a large amount of sensitive data, you need the ability to detect and prevent this action if it’s considered inappropriate. Again, the use of ABAC can provide organizations with preventative controls at the business process, transaction, and master data level. - Perform Risk and Trust Assessments Early in Digital Business Initiatives
This imperative focuses on early risk assessment, meaning performing risk and trust assessments early in the process execution. - Instrument Infrastructure for Comprehensive, Full Stack Risk Visibility, Including Sensitive Data Handling
This is a continuous risk assessment recommendation across the full tech stack and data handling to enable adaptive security decisions. - Use Analytics, AI, Automation and Orchestration to Speed the Time to Detect and Respond, and to Scale Limited Resources
This imperative recommends using artificial intelligence, machine learning, analytics, and automation to increase the efficiency and effectiveness of risk detection, analysis, and response capabilities. - Architect Security as an Integrated, Adaptive Programmable System, Not in Silos
Avoid silos! Organizations shouldn’t perform risk assessments in individual isolated silos. Instead, aggregate continuous risk assessments provide a more accurate view of the organizations’ risk exposure. - Put Continuous Data-Driven Risk Decision Making and Risk Ownership into Business Units and Product Owners
This imperative encourages better transparency and decision-making through better data-driven risk visibility to the business unit leaders for their own decision-making.
How Appsian Security Helps Organizations Achieve Adaptive Security
The problem we help companies overcome: In its current form, the static data protection approach utilized by most organizations lacks the effectiveness required to manage today’s complex challenges. Without an accurate picture of risk exposure in their organization, security administrators protect data the only way they can – with restrictive measures under the principle of least privilege and zero trust.
Here’s how Appsian Security’s capabilities align to the Gartner adaptive security model. The Gartner adaptive security model is illustrated with the Appsian Security solution capabilities aligned with their Predictive & Discovery Requirements, Preventative & Adaptive Access, Detective & Monitor Usage, and Respond & Manage User capabilities.
Five Ways Appsian Security Helps Improve ERP Data Security
Organizations are being challenged to protect access to sensitive and confidential data while improving their ability to analyze security data and detect attacks in progress. Here are five ways that Appsian Security can help your organization meet these challenges:
- The capabilities of the Appsian Security solution align with Gartner’s Seven Adaptive Security Imperatives.
- Appsian offers context-based access controls that can prevent, detect, and respond to user anomalies at the business process, transaction, and data level.
- Appsian enables continuous monitoring and real-time reporting of user anomalies.
- Appsian offers artificial intelligence, machine learning, and automation to increase the efficiency and effectiveness of your risk detection, analysis, and response capabilities.
- Appsian can automate the enforcement of your policy requirements at the business process, transaction, and data level.
Contact Appsian today to learn how our zero trust solutions can anchor your adaptive security architecture and improve your ERP data security.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Zero Trust is a Centerpiece of President Biden’s Latest Executive Order on Cybersecurity
On May 12th, President Biden signed an Executive Order to help improve the nation’s cybersecurity posture and strengthen Federal networks. This order was preceded by several high-profile attacks like SolarWinds and most recently, the Colonial Pipeline – both of which highlighted key deficiencies in the federal government’s ability to detect, respond, and ultimately communicate about cybersecurity threats.
One of the main contentions was around modernizing and implementing stronger cybersecurity standards. Highlighted specifically, was the need to implement zero trust security models and use multifactor authentication (MFA):
The Executive Order helps move the Federal government to secure cloud services and a zero trust architecture and mandates deployment of multifactor authentication and encryption with a specific time period. Outdated security models and unencrypted data have led to compromises of systems in the public and private sectors. The Federal government must lead the way and increase its adoption of security best practices, including by employing a zero-trust security model, accelerating movement to secure cloud services, and consistently deploying foundational security tools such as multifactor authentication and encryption.
What is Zero Trust?
In short, Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters, and instead must verify anything and everything trying to connect to their systems before granting access. Zero Trust is a topic we at Appsian have written about many times, including here.
What is Zero Trust in Practice?
Applications that leverage role-based access controls make enforcing Zero Trust very complicated. Simply because role-based access controls use a static rule set to govern access – and those access privileges do not change dynamically with varying contexts of access. Whether a user is accessing from an unknown network, device, location, outside business hours, etc. – their “originally granted” access privileges remain intact. This is the foundation of risk that Zero Trust is meant to mitigate.
In practice, Zero Trust would require the use of context-aware controls for authentication. Controls that are able to identify contextual variables and apply an additional authentication step prior to granting access to an application or data within the application. So, even if a user’s role-based control said they were allowed to view something, an additional authentication step would be required if any of the contextual variables were indicative of risk. The user is never trusted by default – they must re-authenticate if necessary.
How Does Zero Trust Relate to ERP?
ERP applications like PeopleSoft, SAP ECC, and Oracle EBS were designed years (decades) before Zero Trust was recommended. Meaning, the native architecture does not allow for the seamless integration of multifactor authentication solutions that can A) be integrated at the field/transaction levels of workflows or B) deploy MFA dynamically with each unique context of access. In essence, traditional ERP applications create a significant challenge for Zero Trust.
Appsian Enables Zero Trust in ERP
Requiring dynamic MFA that is integrated inside ERP applications is one of the most common use cases our security platform solves. For over 10 years, Appsian has been working to develop native integrations between Oracle and SAP ERP applications and some of the top MFA providers in the market including Duo, Bio-Key, RSA, Symantec, SecureAuth, and more.
For a demonstration, please reach out to us today! Appsian can help you remain aligned with information security best practices across your ecosystem.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Are ERP Security and Compliance Risks Interfering with Your Digital Transformation?
Implementing enterprise resource planning (ERP) systems has always been both mission-critical and notoriously difficult. They must align with business processes, but the organization distributes those processes across multiple departments. Legacy ERP systems, often considered a large one-time investment, lack the flexibility necessary to scale with your business. As your organization began its digital transformation journey, cloud-based ERP seemed to be a solution to many of these problems. However, every benefit comes with a cost. Modernizing legacy ERP systems for security and compliance creates new challenges, particularly with distributed workforces.
Why is Modernizing ERP a Mission-Critical Business Goal?
Whether you wanted to modernize your ERP or not, you likely found yourself rapidly adopting to remote access requirements in 2020. In response to COVID-driven stay-at-home orders, companies needed to accelerate their digital transformation strategies. This move included ERP systems.
However, as you look toward a post-pandemic business model, you might be considering maintaining a hybrid workforce. Thus, modernizing your ERP is a mission-critical business goal for several reasons, including:
- Ability to access from anywhere
- Built-in Customer Relationship Management (CRM)
- Lower capital expenditures with subscription models
- Reduced total cost of ownership
According to HubSpot’s 2020 ERP Report, 34% of respondents said they were moving away from legacy systems, and 86% selected SaaS deployment models. However, that same report noted that 27% of respondents remaining on-premises cited security breach risk as their reason.
ERP Security and Privacy Controls are Notoriously Difficult to Implement
When undergoing digital transformation, organizations often struggle trying to secure their ERP systems. Most companies need to take a hybrid approach that connects their legacy on-premise deployment to their new SaaS applications.
Organizations struggle trying to prioritize and mitigate risks for several reasons. However, three fundamental challenges exist:
- Data storage arrangements: Inability to control infrastructure increases data leakage and corporate espionage risks
- Authentication: Continued brute force attacks and credential theft increase data security and privacy risks
- Access controls: Complex identity and access relationships reduce the ability to control who accesses resources
Traditional on-premise ERP deployments used role-based access controls (RBAC) with static permissions lists. However, the inherently static nature means that these alone fail to protect data, particularly in remote or hybrid work environments.
For example, PeopleSoft’s security model assigns roles to user profiles. The user profile defines the data that the person can use. The permissions list is the set of pages the user can access and actions the user can take.
These controls protect data across on-premises deployments where the applications and users sit inside the organization’s network. Since remote access to on-premise ERP is dynamic, these legacy controls increase security and privacy risks when implemented for modernized ERP projects.
5 Strategies for Setting Security and Privacy Controls for a Hybrid ERP Deployment
Companies adopt digital transformation to leverage speed and agility, enabling them to scale operations. At the same time, they still need to maintain their on-premise systems. To protect information, organizations need dynamic and scalable access controls that align with their systems and business goals.
1. Identify Assets and Assess Risk
For effective access controls, the first step is to identify all data that you store, process, and transmit. Second, you need to assess the data’s criticality and risk level. Finally, you need to identify users who access information and assess the risk they post to the organization.
As part of this, you should consider:
- Standard users
- Privileged users
- Users’ payment processing authority level
- Financial information
- Personally identifiable information
- Sensitive corporate information
Once you assess user and data risk, you can create a plan that helps you migrate the information securely. When setting controls, you should limit access according to the principle of least privilege and create fine-grained access privileges.
2. Normalize Data Access Across Integrated Applications
With SaaS applications, organizations no longer need to commit to a single platform. They can pick and choose the applications that best meet their needs, which can mean integrating multiple vendors.
As you build out your application stack, you need to maintain appropriate access controls. This can be difficult when vendors define access rights differently. Many organizations worry that normalizing access data requires an expensive, labor-intensive overhaul of their Identity and Access Management programs.
However, if you focus on visibility instead of connectivity, you can leverage automated tools that help you see into user access. Tracking user access in a single location, despite disparate access definitions, enables you to protect data security and privacy even across different application vendors like SAP and PeopleSoft.
3. Use Context
A primary benefit of hybrid on-premise and cloud ERP systems is the ability for people to work wherever they want. However, that same flexibility drives many of the security and privacy risks companies face.
Adding context to your access permissions is another way to secure data. After setting your role-based controls, you should consider adding context such as time of day, geographic location, and IP address. With these attribute-based access controls (ABAC), you can more granularly define how users interact with data, making it easier to detect anomalies.
4. Enable Step-Up Multi-factor Authentication
ABAC also enables you to use step-up multi-factor authentication (MFA). Step-up authentication is a process where users need to re-authenticate into an ERP application when they attempt a privileged function or transaction. ABAC enables you to trigger step-up MFA when your system detects an abnormal attribute, often one associated with credential theft.
For example, one of your users always logs in from California, USA. If the user tries to access the ERP’s payment module from Ontario, Canada, the system will notice that this is an outlier, an abnormal attribute for this user. The system can require re-authentication, additional proof that the person is who they say they are. If this is a cybercriminal leveraging stolen credentials, then the step-up authentication acts as an additional security and privacy control, preventing unauthorized access.
5. Continuously Monitor Behavior Around Data Access and Usage
Modernizing your ERP security and privacy controls also includes continuously monitoring for anomalous and suspicious activity. Gaining a granular view into data access and use is a way to proactively mitigate risks that can arise in a remote workforce accessing ERP solutions.
Continuously monitoring access can help you gain insight into employee productivity, cybersecurity risks, and insider fraud. Tracking when and how employees use data gives you a way to set baselines for “normal” activity—any deviations from this warrant further investigation.
For example, a user consistently accesses your ERP between 8 am and 5 pm from a location in the United States. If the user suddenly accesses the system at 2 am, the anomalous activity could indicate fraud. Even if you’re using step-up MFA to prevent that activity, you still need to investigate the event. While it may be someone with insomnia, it can also be an employee trying to steal information or money.
Appsian Enables ERP Security and Compliance for Your Digital Transformation
Modernizing your legacy ERP application doesn’t mean you have to “sacrifice” the same granular levels of control and visibility as a cloud application to enforce data security, privacy, or compliance policies. Taking a proactive approach to ERP security and data privacy during your company’s digital transformation can mitigate risks before they turn into realities.
Appsian has been enhancing on-premise ERP environments for more than ten years, and we’d love the opportunity to learn more about your digital transformation project so we can help you manage your ERP data security and compliance needs. Contact us today.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
It’s Time to Include Data in the ERP Security Conversation
ERP security had traditionally focused on vulnerability testing for ERP applications, whether hosted on-premise or in the cloud. Given the sensitive nature of ERP transactions, frequently checking applications, databases, and servers for vulnerabilities through routine assessments had long been considered best practice. It makes sense that application vulnerabilities are considered a top threat vector because ERP applications were long touted for their highly customizable nature. Customizable because every organization’s business requirements are different – which means security settings and access controls need to be highly customizable.
All of this customization was in-service to governing user access to the application – a real “outside looking in” approach. But if you’re constantly looking “out” for threats, how do you protect against the ones that are already “in?”
Is Traditional ERP Security Actually Protecting Data?
While you might be checking for conflicts in your configuration settings, ensuring you’re up-to-date on vendor patches, and executing manual audits every once in a while, you should ask yourself, “am I actually protecting my ERP data?” Sure, preventing intrusions is passively protecting ERP data. But at the end of the day, if you spend your time hardening the walls of your fortress, you’re really only protecting the perimeter of your fortress – not what’s inside. Cybercriminals have identified this disconnect and now spend their time exploiting user credentials to infiltrate systems to steal and manipulate data. Cybercriminals have adjusted. Now it’s time organizations do the same with their ERP applications, and ultimately – their ERP data.
The Information Security Conversation is Going Below the Network & Application Layer
Information security professionals have long been adept at protecting enterprise data and not just network and application perimeters. The abundance of cloud applications has allowed access controls and visibility to go to the next level. Concepts like zero trust and least privilege all require information security policies that are not reliant on arbitrary roles and privileges but on inspecting who a user is, where they are coming from, on what device, and any other attribute. Just because they are allowed access to a network or application does not grant them privileges to data.
If this is where the information security conversation is going, why is ERP security still focused on the perimeter? Shouldn’t the focus be on ERP data security?
How to Shift the Conversation to ERP Data Security
Many would say that ERP security remains a perimeter conversation because such a large part of the ERP market uses on-premise applications. This dates back to the inception of ERP when the appeal was mostly around customizing your business transactions to your processes. This would be accurate – but as business became more complex, organizations became more entwined with their legacy applications. However, that doesn’t mean that on-premise applications (and ERP applications only hosted in the cloud) must remain isolated from a unified “ERP Data Security” conversation.
Here Are a Few Recommendations for Beginning an ERP Data Security Conversation:
- Integrated Identity & Access Management (IAM) – Integrating enterprise solutions meant for identity and access management (ex. SSO & MFA) provides a perfect opportunity to govern access to data versus only governing access to an application. An integration would enable policies to be written that deploy authentication measures based on what someone is attempting to access. This is also referred to as “step-up authentication” or zero trust. Of course, an integration layer is required, which is exactly why Appsian developed the necessary integration connections that organizations can use to natively integrate their IAM solutions with their legacy ERP applications (i.e., Oracle PeopleSoft & E-Business Suite).
- Attribute-Based Access Controls (ABAC) – Traditional ERP governance revolves around role-based access controls. Pre-defined and sometimes over-simplified buckets that dictate what users can and can’t do. Role-based access controls (RBAC) are artifacts of traditional ERP security strategies that have been identified as problematic and flawed when data protection is the objective. This is not to say that RBAC doesn’t have its place but as a sole governance measure? Absolutely not. Many would say that the rapid move to remote work following COVID-19 was the death blow to RBAC because so much of its effectiveness hinges on network and application security layers. Both of which enter a grey area when sensitive financial transactions and data can be accessed remotely.
To help organizations manage, and more importantly, mitigate the risk of remote access to financial applications like SAP ECC, S/4HANA, & E-Business Suite, Appsian has developed Attribute-Based Access Controls that organizations can use to grant, modify, or restrict access to data. Governance policies can be dynamically enforced based on the context of user access – or attributes of user access.
- Data Level Visibility is Critical – ERP applications are no stranger to activity logging. However, current logging is primarily in-service to troubleshooting system issues and receiving basic insight on authentication and page access. This is why auditing an ERP application requires manual pulling and triangulation of reports from multiple sources. It’s an obstacle most have to accept, and because of this, they only audit sporadically.
To gain visibility and insight into how data is being accessed and used, Appsian developed Appsian360. Appsian360 represents a powerful combination of comprehensive user activity logging and analytics – all designed to detect and alert to anomalous behavior. Whether it’s access from a foreign country, the same user frequently downloading certain reports, or specific PO or account numbers receiving frequent access, Appsian360 is designed to give ERP customers the data level visibility needed to automate critical security, compliance, and audit functions.
Appsian Helps Enable ERP Data Security
Just because your organization is using a legacy ERP application does not mean that you cannot employ the same granular levels of control and visibility as a cloud application. Appsian has been enhancing on-premise ERP environments for over 10 years, and we’d love the opportunity to learn more about your ERP data security objectives. Contact us today!
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives