How Identity Governance and Administration (IGA) Compliments IAM to Improve Data Security
Identity, Governance, and Administration (IGA) is defined by Gartner as an “activity within the identity and access management function that concerns the governance and administration of a unique digital representation of a user, including all associated attributes and entitlements.” In simpler terms, IGA capabilities help organizations govern and monitor user activities inside the application to detect and respond to user behaviors or policy violations.
IGA is a superset of Identity and Access Management (IAM) and was born out of the need to extend data security and compliance practices within applications. IGA goes beyond IAM control measures to monitor user activity within a given application and implement controls that enable governance and policies at a granular level.
How IGA Enhances Data Security in ERP Applications
Reduces Risk of Data Access
Traditional IAM solutions verify the user’s identity and, once verified, provide access to ERP applications based on the roles assigned to that specific user. Consequently, the user gains access to all authorizations allowed by their roles. The IAM solution has little to no control over what the user does once access has been granted. This creates a governance challenge and increases the overall risk significantly.
The Appsian Security Platform builds on existing Role-Based Access Controls (RBAC) to create a security layer based on the context of access, such as time, device, location, IP address, etc. Using Attribute-Based Access Control (ABAC), Appsian allows you to restrict and/or mask user access to sensitive data at the page and field level inside your ERP applications. This gives security teams the controls they need to not only determine risk but also mitigate it across ERP applications.
Enables Layered, Policy-Based Security Controls
The ability to orchestrate and enforce policies within your ERP ecosystem is key to controlling user access to data and transactions. This is especially true when companies must follow mandatory data privacy regulations like CCPA, GDRP, and Sarbanes Oxley. Without the necessary governance and controls in place, companies could face audit failures and huge fines, not to mention the loss of customer trust.
The Appsian Security Platform allows you to implement layered security controls within your ERP applications. The platform’s ability to mask data at the field level shields sensitive PII data like Social Security Numbers, bank account details, etc. While the Click-to-View feature allows users to view data when needed, it also creates an access log that helps security teams detect suspicious user activity. Appsian also enables you to implement in-line authentication challenges to perform sensitive transactions. In addition to creating layered security controls, these features also provide a reliable audit trail and enhance compliance.
Streamlines User Authorizations
User authorization is an integral part of IAM, but once the authorizations have been granted, traditional IAM solutions offer minimal insights into how these authorizations are being used. Granting new authorizations to users, also known as user provisioning, is usually a manual process that directly impacts Segregation of Duties (SoD). In many companies, the volume of authorization requests that ERP admins receive is so overwhelmingly high that it results in users being over-provisioned, i.e., having more authorization than they need. This increases your overall data access risk and leads to SoD violations that eventually become the cause of serious compliance deviations and audit failures.
To overcome this governance challenge, the Appsian Security Platform enables you to monitor authorization usage in real-time. The platform’s adaptive security provides a 360° view over authorization and behavior-based user activity to detect SoD violations while providing steps for remediation. Appsian also deploys Artificial Intelligence (AI) and Machine Learning (ML) to create user profiles which are then analyzed to recommend removal of unused authorizations and detect deviations in authorization usage. Appsian automates the tediously manual ERP authorization management process while decreasing the risk to data access and enabling higher compliance standards.
Schedule a demo with our security experts to find out how Appsian’s adaptive security enhances data security and compliance within your ERP applications.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How to Protect Your ERP With an Adaptive Security Model
Agility is the name of the game in today’s ERP data security landscape. Organizations are being challenged to detect threats as they happen, quickly address vulnerabilities, and continuously improve their security posture while protecting crucial ERP data as well as their overall business. One strategy that is helping organizations become more proactive is aligning to an adaptive security model.
Focused on operationalizing agile, context-aware, and adaptive technologies, an adaptive security model enables organizations to strengthen security and leverage automation for continuous improvement.
What is Adaptive Security?
Adaptive security is an approach to managing security that analyzes behaviors and events to protect against and adapt to threats before they happen. With an adaptive security architecture, an organization can continuously assess risk and control effectiveness monitoring and automatically provide proportional enforcement that can be dialed up or down to fit its need.
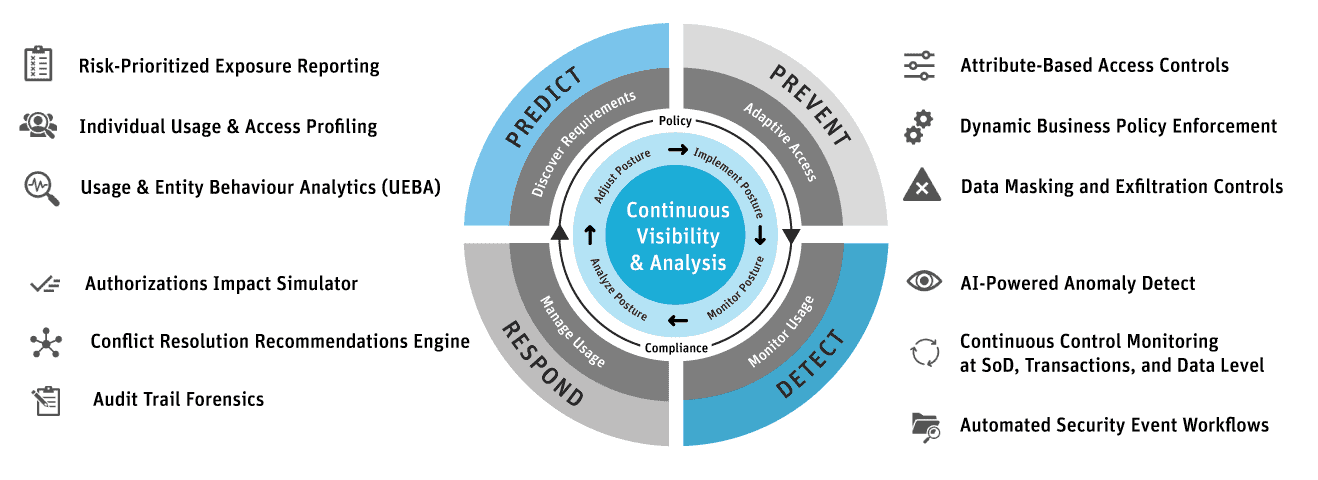
Figure 1: Adaptive Security Architecture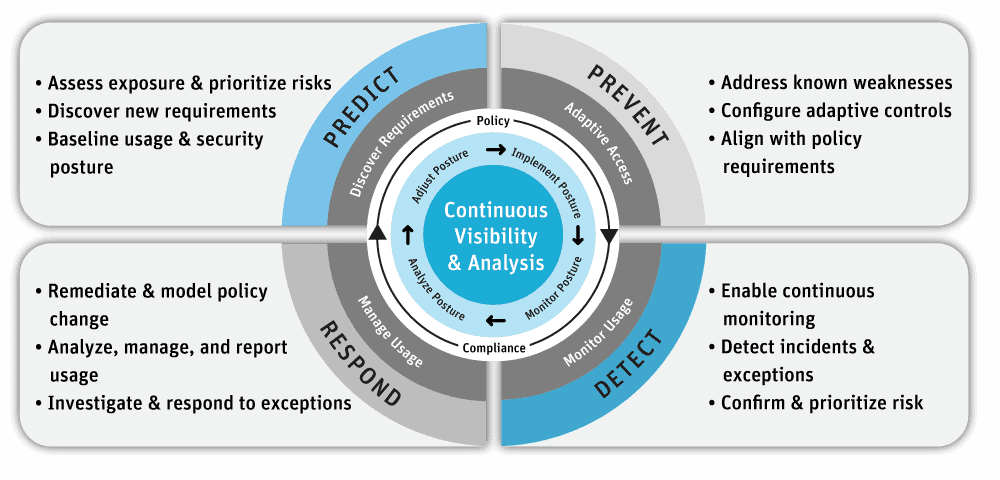
You’ll note that there are four stages of an adaptive security architecture: Prevent, Detect, Respond and Predict. These stages help organizations transform the old static, roles-based approach to ERP data security to a continuous monitoring and risk-adaptive approach. Zero trust is a core concept to adaptive security, which promotes continuous monitoring and analysis as a starting point, enables rapid detection of behavioral anomalies, and permits rapid responses to quickly stop and resolve security incidents.
Seven Imperatives for an Adaptive Security Architecture
According to Gartner, supporting digital business transformation in an environment of advanced threats requires a new approach for all facets of security. Security and risk management leaders can use these seven imperatives of an adaptive security model to embrace the opportunities and manage digital business risks. Each imperative is Gartner’s recommended capability required of your ERP security, risk & compliance solution to enable the security model.
- Replace One-Time Security Gates with Context-Aware, Adaptive, and Programmable Security Platforms
Organizations need to replace the initial one-time, yes/no risk-based decision at the main gate to their systems (typically managed by a static authentication and authorization process) with a continuous, real-time, adaptive risk and trust analysis of user anomalies with context-aware information across the platform. Context-aware security (also known as attribute-based access controls or ABAC) uses situational information, such as identity, geolocation, time of day, or type of endpoint device. - Continuously Discover, Monitor, Assess and Prioritize Risk — Proactively and Reactively
Risks events are fluid and require constant identification, analysis, prioritization, monitoring, and response after the initial login assessment. This should include a combination of proactive and reactive capabilities. For example, if a user attempts to download a large amount of sensitive data, you need the ability to detect and prevent this action if it’s considered inappropriate. Again, the use of ABAC can provide organizations with preventative controls at the business process, transaction, and master data level. - Perform Risk and Trust Assessments Early in Digital Business Initiatives
This imperative focuses on early risk assessment, meaning performing risk and trust assessments early in the process execution. - Instrument Infrastructure for Comprehensive, Full Stack Risk Visibility, Including Sensitive Data Handling
This is a continuous risk assessment recommendation across the full tech stack and data handling to enable adaptive security decisions. - Use Analytics, AI, Automation and Orchestration to Speed the Time to Detect and Respond, and to Scale Limited Resources
This imperative recommends using artificial intelligence, machine learning, analytics, and automation to increase the efficiency and effectiveness of risk detection, analysis, and response capabilities. - Architect Security as an Integrated, Adaptive Programmable System, Not in Silos
Avoid silos! Organizations shouldn’t perform risk assessments in individual isolated silos. Instead, aggregate continuous risk assessments provide a more accurate view of the organizations’ risk exposure. - Put Continuous Data-Driven Risk Decision Making and Risk Ownership into Business Units and Product Owners
This imperative encourages better transparency and decision-making through better data-driven risk visibility to the business unit leaders for their own decision-making.
How Appsian Security Helps Organizations Achieve Adaptive Security
The problem we help companies overcome: In its current form, the static data protection approach utilized by most organizations lacks the effectiveness required to manage today’s complex challenges. Without an accurate picture of risk exposure in their organization, security administrators protect data the only way they can – with restrictive measures under the principle of least privilege and zero trust.
Here’s how Appsian Security’s capabilities align to the Gartner adaptive security model. The Gartner adaptive security model is illustrated with the Appsian Security solution capabilities aligned with their Predictive & Discovery Requirements, Preventative & Adaptive Access, Detective & Monitor Usage, and Respond & Manage User capabilities.
Five Ways Appsian Security Helps Improve ERP Data Security
Organizations are being challenged to protect access to sensitive and confidential data while improving their ability to analyze security data and detect attacks in progress. Here are five ways that Appsian Security can help your organization meet these challenges:
- The capabilities of the Appsian Security solution align with Gartner’s Seven Adaptive Security Imperatives.
- Appsian offers context-based access controls that can prevent, detect, and respond to user anomalies at the business process, transaction, and data level.
- Appsian enables continuous monitoring and real-time reporting of user anomalies.
- Appsian offers artificial intelligence, machine learning, and automation to increase the efficiency and effectiveness of your risk detection, analysis, and response capabilities.
- Appsian can automate the enforcement of your policy requirements at the business process, transaction, and data level.
Contact Appsian today to learn how our zero trust solutions can anchor your adaptive security architecture and improve your ERP data security.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives