6 Warning Signs of PeopleSoft Privileged Account Misuse
Privileged user accounts are hacker magnets. With cyberattacks getting more targeted and sophisticated, intruders can easily bypass traditional authentication measures. So it’s no wonder that 74% of data breaches stem from privileged account abuse by external hackers and insiders with elevated privilege (according to the 2021 Verizon Data Breach Investigations Report).
Why Compromised Account Activity Is Difficult To Detect In PeopleSoft
PeopleSoft applications usually offer limited monitoring and logging capabilities. Once a user is authenticated at the front door, it is difficult to track their activities within the system. This creates blind spots that allow the bad actors to stay undetected for months or years. A viable solution is to continuously monitor user activity around data access and usage inside PeopleSoft.
6 Warning Signs Of Privileged Account Misuse
When companies monitor outlier behavior patterns, they are more likely to detect compromised accounts or possible malicious activities. This reduces the discovery and containment time and cost. Here are six key signs to monitor that could indicate privilege account misuse in PeopleSoft.
1. Questionable Login Patterns
Always watch out for privileged users trying to log in to PeopleSoft applications outside their working hours. For example, a system admin logging in at 3:00 AM on a Sunday should trigger an alert. Additionally, sudden changes in IP address, location, device, etc., could be possible indicators of privilege account misuse.
2. Deviation From Normal Activities
Let’s say Paula from the HR department needs access to an employee’s payroll information to do her job. You find her trying to access the data outside of her login hours from a suspicious IP address. This could be a sign of privilege misuse.
3. Unusually Long Or Short Session Length
Privileged PeopleSoft users typically have a fixed set of activities. This means the duration a particular application or session is active and a specific credential is logged in could indicate malicious activities. Granular details with logs that capture employee session lengths can differentiate between normal and malicious activities.
4. Unauthorized Changes To Master Data
PeopleSoft applications often have large volumes of sensitive master data stored across multiple siloes. Any changes to master data, such as adjusting a PO amount beyond limits and direct deposit changes, need to be investigated.
5. Unusual Data Downloads And Query Running
Running queries and downloading sensitive PeopleSoft data to unauthorized devices, outside of business hours, and from unknown locations are a few warning signs of privilege abuse. In addition, an employee using unapproved workarounds for transferring data to cloud storage accounts for easy access often leaves critical data and PII vulnerable to attackers.
6. Frequently Failed Attempts At Logging Into Critical Applications
You would typically flag failed password attempts by an external user. Similar attempts by internal privileged users, however, do not raise eyebrows. PeopleSoft passwords being inherently weak, usually become the targets for attack. Erratic behaviors indicating compromised privileged accounts should always generate alerts.
How to Detect and Prevent Privileged Account Misuse in PeopleSoft
Attackers always try to make anomalous behavior appear routine and normal. To protect your PeopleSoft applications, begin with monitoring your privileged user accounts to uncover hidden business risks and data security threats in real-time. Appsian Real-Time Analytics offers the following capabilities to mitigate privileged user risk across your PeopleSoft ecosystem:
- Continuously monitoring privileged user activity and behavior at a granular level provides visibility into what they do with their access and how they engage with data.
- Detailed logs to capture granular transaction details like discounting, PO amount increases, recurring purchases, etc.
- Track all the user access data points with dashboards to track off-peak access, strange IP address access, and access from unknown locations.
The next step is to prevent improper activity by adopting a layered, data-centric security model that includes –
- Enhanced access controls with dynamic authorization policies
- Expanded use of data masking to all fields considered personally identifiable
- Stepped-Up Multi-Factor Authentication to prevent unauthorized access
Schedule a demo with our security experts to mitigate privileged user risk across your PeopleSoft ecosystem.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How FTC Updates to “Safeguards Rule” Impact Higher Education Institutions
On December 9, 2021, the Federal Trade Commission (FTC) published a final rule amending the requirements for safeguarding customer information under the Gramm-Leach-Bliley Act (GLBA) (the Safeguards Rule). The Safeguards Rule has long specified cybersecurity standards under which financial institutions must maintain customer information, including higher education institutions (thanks to their participation in the federal student financial aid program). This is a significant development for our Higher Ed customers because it effectively mandates any Title IV participating institution to follow the updated guidelines.
Obligatory disclaimer: This article isn’t legal advice. Instead, it is a high-level look at new security regulations that affect our higher education customers. Therefore, we recommend that you seek guidance from your legal department and other relevant experts.
Key Security Elements of the Updated Safeguards Rule
While the amendments still allow some flexibility, they now include detailed criteria that higher education institutions must implement. This includes more detailed requirements for developing and establishing an information security program. Here’s a brief look at some of the security elements from the updated Safeguards Rule that higher education institutions should be aware of:
- 314.4(c) Implement and maintain technical and physical access controls on customer information to limit access to authorized users and limit those users’ access to the scope of their authorizations.
- 314.4(c) Implement measures to “monitor and log the activity of authorized users” and to detect when they have accessed, used, or tampered with customer information outside the scope of their authorization.
- 314.4(c) “Implement multi-factor authentication for any individual accessing any information system.”
- 314.4(d)(2)—Implement continuous monitoring of “information systems” (as defined in 314.2) or annual penetration testing with vulnerability assessments at least every six months.
- 314.4(f)(3)—Periodically assess the information security risks that your institution’s service providers present and the adequacy of the safeguards they deploy to ensure that they are following the provisions of the Rule.
- 314.4(f)(3)—Periodically assess the information security risks that your institution’s service providers present and the adequacy of the safeguards they deploy to ensure that they are following the provisions of the Rule.
Appsian can help organizations with these requirements. Here’s how:
- Implementing fine-grained, dynamic (ABAC) controls while continuing to leverage the role-based controls that are already defined and in-use across the organization.
- Implementing dynamic MFA, not just at the perimeter but also at the application, transaction, and data level (inline.)
- Granular Activity Logging to provide visibility into data access and usage trends
- Real-time user activity monitoring to ensure that security controls are properly enforced
- Audit trail to aid investigation and remediation efforts
What Else is Included in the Updated Safeguards Rule
In addition to specific security controls, the amendments also include new requirements for risk assessments and new accountability and reporting requirements to boards of directors. We encourage you to review the revised regulations because some parts of the amendments may be more relevant to your institution’s needs than others. (pages 109–128 of this PDF document specifically cover the new rule)
Effective Date of the Updated Safeguards Rule
Due to the time required to implement many of the described provisions, the effective date of most above-described elements is December 9, 2022.
Next Steps
You don’t want to wait until the last minute to implement any of these security mandates. Contact us today to learn how we can help ensure that your information security program meets these new federal requirements.
Sources, References, and Further Reading:
- “Policy Analysis: Revised, Highly Prescriptive FTC Safeguards Rule,” by Jarrett Cummings, EDUCAUSE
- “FTC Updates to “Safeguards Rule” Has Impacts for Higher Education Institutions,” by Sarah Pheasant & Jonathan Tarnow Faegre, Drinker Biddle & Reath LLP
- Standards for Safeguarding Customer Information (PDF) by The Federal Trade Commission
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How Appsian Solved University of Nebraska’s Unique SAML Authentication & IdP Configuration
The University of Nebraska uses PeopleSoft Campus Solutions for its student information system and wanted to streamline authentication for students, faculty, and staff across eight separate campus locations. So, they turned to a single sign-on integration solution from Appsian that enhanced security practices but was flexible enough to allow the eight campuses to retain the Identity Provider (IdP) of their choice.
Centralized SAML Authentication & Scalability: The Missing Pieces
When the University approached Appsian for a SAML SSO, they were currently using a custom, home-grown solution. This solution was not scalable in the long term and created a significant amount of complexity.
Our team realized that the University of Nebraska was struggling with three key challenges –
- The University uses two instances of PeopleSoft – One for the University System (five campuses) and one for the State College System (three campuses).
- Each campus has its own PeopleSoft Internet Architecture (PIA) within its designated instance of PeopleSoft.
- The University utilizes eight different Identity Providers (IdPs) across all locations.
To streamline the SAML authentication process and improve the user experience across multiple applications, the University had to reduce the overall number of authentications by centralizing authentication management from a common platform. The University’s IT security leadership was impressed with Appsian’s ability to provide continuous support and offer creative and sustainable alternatives to offer the best solution for SAML integration.
Solving the University’s Unique IdP Configuration
The University’s security team was looking for PeopleSoft SAML integration to deliver a single sign-on solution that met their unique configuration requirements. Appsian’s solution was attractive to them since it was native to PeopleSoft. It enabled all eight campuses to retain the IdP of their choice. In addition, they could map to any one of the eight PIA instances.
“Instead of viewing our unique configuration as “the client’s problem,” Appsian looks for creative and sustainable alternatives to provide the best solution,” said William Barrera Fuentes, Director of the Nebraska Student Information Systems.
We enabled some unusual configurations that ensured all eight campus locations (and PIAs) could keep using their IdPs without sacrificing security or flexibility. Their team was happy that the cost of ownership did not increase by deploying additional infrastructure to support SSO and SAML authentication.
Native SAML Compatibility for PeopleSoft & Secure SSO With Appsian
Appsian’s PeopleSoft customer base includes multiple organizations in the education sector like the University of Nebraska looking for a configurable SSO solution with no custom development. With Appsian’s PeopleSoft SSO Connector, organizations can:
- Leverage existing investment in SSO solutions to authenticate PeopleSoft sessions via SAML-based Identity Providers
- Access PeopleSoft via deep link navigation (sent by email or other communication channels)
- Support multiple IdPs concurrently for consolidated systems with separate user groups
- Deploy your multiple IdP’s SSO in PeopleSoft as quick as 7 days with no additional hardware or custom coding
Schedule a demo with our experts to learn how Appsian integrates native SAML functionality in PeopleSoft to deliver a seamless Single Sign-On.
Customer Profile:
The University of Nebraska is the state’s only public university system, consisting of five campuses, each with a distinct role and mission. Together the campuses enroll 51,000 students and employ 16,000 faculty and staff who serve the state and world through education, research, and outreach.
Related Reading: University of Nebraska Case Study
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How Appsian Implemented Dynamic Data Masking to Help The State of Kansas Secure Sensitive PeopleSoft Data
Like most state governments, the State of Kansas wanted employees and non-employees to access PeopleSoft self-service within and outside the corporate network. They encountered a common challenge: How do they roll out PeopleSoft self-service to a massive audience while still protecting their data and addressing compliance risks. To fortify their PeopleSoft environment and secure remote access and their data, the State approached Appsian for their dynamic data masking tools.
Requirements for Dynamic Data Masking
Over a two-year period, the State expanded access to PeopleSoft from 12,000 to all 50,000 state employees, including contractors, truck drivers, police officers, and state police medical contractors who would be using iPads and various mobile and remote workstations.
However, they did not have any third-party data masking tool for their production or non-production environment. Additionally, the masking capability in their existing PeopleSoft environment presented the following challenges –
- Masking was incomplete
- It offered no flexibility
- The feature only worked on select delivered pages
The native masking functionality was not working sufficiently for their HCM and FSCM power users. In addition, as their roles were getting more complex, access control became a critical requirement that out-of-the-box PeopleSoft features could not fulfill.
The State Of Kansas Enhanced PeopleSoft Security With Dynamic Data Masking
The State deployed MFA capabilities, contextual data masking, and dynamic access controls to fill the security gaps in access control and usage. The State also used the Appsian Security Platform to improve remote access control, manage risk exposure, and increase the visibility of user activity in their FSCM and HCM pillars.
Following the implementation of Appsian’s Dynamic Data Masking tools and capabilities, the State of Kansas is now able to achieve the following –
- Leverage existing static data masking to challenge users to reconfirm identity at a page level
- Location-based security to protect access to certain pages for users outside the State’s network
- Better visibility into the activities of privileged users while allowing them to access sensitive data to perform their roles efficiently
Appsian is a Key Enabler For PeopleSoft Data Security & Compliance
Appsian’s PeopleSoft customer base includes multiple organizations in the government sector like the State of Kansas looking for a single platform to strengthen remote access management, data security, and compliance, including:
- Native SAML/ADFS Compatibility And PeopleSoft MFA Integration: Integrating single sign-on and multi-factor authentication natively with PeopleSoft and your identity provider improves security and convenience. Integrated MFA also enables step-up authentication, so users can be forced to re-authenticate when accessing highly sensitive transactions.
- Contextual Access Control For Greater Security: Reduce the attack surface with dynamic data masking tools that take into account the contextual variables of a user’s access and define privileges in real-time. Implement least privilege to limit access to modules/transactions, dynamically mask sensitive data, enforce step-up MFA, and more.
- Real-Time Analytics For Improved Response Times: Enhanced PeopleSoft logging capabilities capture all user activity at the field, page, and component levels and combine them with contextual user data. Real-time visualized dashboards allow you to quickly spot suspicious activity and drill down to root out issues.
Contact Appsian’s PeopleSoft experts today to learn how the Appsian Security Platform can help you establish a dynamic data masking solution.
Customer Profile:
The State of Kansas administrative office comprises over 100 state agencies to provide exceptional community, family, health, education, security, transportation, and more services to the citizens of Kansas.
Related Reading: State of Kansas Case Study
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] How Appsian Helped OU Secure their PeopleSoft Data by Integrating Duo Security (for Dynamic MFA)
Since 2008, the University of Oklahoma Health Sciences Center (OUHSC) has successfully used the Appsian Security dynamic MFA solution to secure the ERP data on its instance of PeopleSoft. OUHSC initially selected Appsian Security because of its ability to directly integrate its multi-factor authentication (MFA) solution with PeopleSoft without added customizations, hardware, or complexity.
What Challenges Made OU Enable Dynamic Access Controls?
OU’s main campus in Norman had its own PeopleSoft system, which was separate from the OU Health Sciences Center’s system. Recently, the University decided to consolidate the Financials and Human Capital systems along with information technology of the University’s three campuses, including uniting the unique instances of PeopleSoft into a single one.
In 2020, the University began the consolidation project. In addition to requiring secure access to the HRMS pillar for the nearly 15,000 faculty and staff members on the unified instance of PeopleSoft, the University wanted to leverage dynamic access controls to enforce MFA at login and inside the application at the field, page, and component levels.
As a unified system, OU wanted to –
- Reduce unwanted exposure of sensitive data
- Improve visibility into user activity across applications
- Limit access to sensitive transactions
Oklahoma University Enhanced PeopleSoft Data Security With Dynamic MFA
Appsian Security’s native integration with PeopleSoft allowed OU to successfully deploy their MFA solution for the HRMS pillar. The University uses MFA at login for both off-campus (remote) and on-campus users. The combined platform for all three campuses applies dynamic access controls to grant access to sensitive information and gate high-value transactions, such as direct deposit, based on contextual attributes like device, geolocation, time, and more. Additionally, OU uses Appsian Security to monitor and log high privileged user activity within PeopleSoft. The system captures all user activity at the field, page, and component levels.
The University completed its system upgrades and merger and is now live using the Appsian Security Platform in all three of its PeopleSoft pillars, namely Financials, Human Capital, and Campus Solutions.
Appsian Security Platform As A Key Enabler For End-To-End PeopleSoft Data Security & Compliance
Appsian’s PeopleSoft customer base includes multiple colleges and universities like Oklahoma University looking for a single platform to strengthen Identity and Access Management, Data Security, and Compliance, including:
- Native SAML/ADFS Compatibility And PeopleSoft MFA Integration: Integrating single sign-on and multi-factor authentication natively with PeopleSoft and your identity provider improves security and convenience. Integrated MFA also enables step-up authentication, so users can be forced to re-authenticate when accessing highly sensitive transactions.
- Contextual Access Control For Greater Security: Reduce the attack surface with a dynamic rules engine that applies the contextual variables of a user’s access and defines privileges in real-time. Implement least privilege to limit access to modules/transactions, dynamically mask sensitive data, enforce step-up MFA, and more.
- Real-Time Analytics For Improved Response Times: Enhanced PeopleSoft logging capabilities capture all user activity at the field, page, and component levels and combine them with contextual user data. Real-time visualized dashboards allow you to quickly spot suspicious activity and drill down to root out issues.
Contact Appsian’s PeopleSoft experts today to learn how the Appsian Security Platform can help you establish a dynamic MFA solution and a strong ERP data security posture.
Customer Profile:
Founded in 1890, the University of Oklahoma is a public research university located in Norman, Oklahoma, just 20 minutes south of Oklahoma City. With three campuses in Oklahoma, OU also offers study abroad opportunities at several locations and OU campuses overseas. The OU Health Sciences Center serves approximately 4,000 students in more than 70 undergraduate and graduate degree programs on Oklahoma City and Tulsa campuses.
Related Reading: OU Case Study
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Why You Should Avoid Customizing PeopleSoft to Enable Single Sign-On (SAML/ADFS)
Don’t Risk the Security of your Data with Customized SSO SAML/ADFS Integration for PeopleSoft
I was on a recent discovery call, and the Senior Software Engineer shared how they’re “ripping out” a custom-built PeopleSoft single sign-on solution (SSO). After acquiring an enterprise SSO, they attempted to build a custom integration with PeopleSoft that presented far more challenges than benefits – especially when users attempted to access with a deep link. Now they’re looking to remove the solution along with the additional infrastructure that was required.
And here’s the sad part: they’re not the first organization I’ve encountered that are experiencing the same challenge. Across all verticals including healthcare, higher education, government, retail and more – PeopleSoft customers are rethinking their decision to enable their enterprise SSO solutions with custom coding, external gateway agents, and reverse proxies. Alternatively, implementing solutions that feature native SAML/ADFS authentication handlers.
Your Custom Single Sign-On Integration Was Not Designed with ERP Data Security in Mind
These projects often start with the IT department recognizing that it can solve a business requirement by building the solution themselves or by using a generic gateway with copy-and-paste code off an internet forum. The main motivation? They possibly save the company some money, bypass the need for approvals or budget, and check a project off their list. Easy-peasy, right? As highlighted in the example above, it’s not always that straightforward.
Often, these projects lack a thoughtful mindset and instead leverage code that is many years old, unsupported, and public to developers and hackers alike. Here lies one of the biggest problems with customizing PeopleSoft for SSO authentication. Getting the integration to work “well enough” is often the goal, and since developers are not information security professionals – they may not have considered the ramifications of using code that hackers can reverse engineer, potentially exploiting loopholes to gain unauthorized access. As a former PSAdmin who personally retrofitted a custom PeopleSoft SSO solution in my past life, I can tell you that security implications are not at the forefront. Between IT wanting to be a good partner to the business and drowning in long-haul projects, “good enough” was often the goal.
The “Typical” Custom PeopleSoft Single Sign-On Approach
There are a few ways to approach building a custom SSO solution. You could try linking SAML open-source code libraries, using reverse proxies, or having an external agent handle it. These solutions seem relatively simple at the outset, but the introduced vulnerabilities are often not obvious or ignored. The end result is that the SSO “works” but is plagued by technical, functional, and security issues once in production.
Linking SAML Open Source Code Libraries
A custom coding project typically begins with a review of PeopleBooks and a Google search to find a relatively quick way to write the code. PeopleCode allows you to link external open-source java libraries inside PeopleSoft. This is code that you’re literally pulling from an old blog and has not been reviewed since the author first published it. Imagine using code from 2007 to secure your custom PeopleSoft single sign-on project. It would never pass a security review!
Secondly, developing a solution yourself is tricky. It isn’t easy to write software that deals with passwords, identity, and authentication. Reputable IdPs spend tens of thousands of man-hours designing, coding, and testing, then supporting their solutions. The lone developer who built your custom solution is now responsible for supporting, maintaining, and upgrading the code. That’s excellent job security for him but a security liability for you.
Reverse Proxies, Gateways, and External Authentication Agents
This one is probably a favorite with system administrators who want to support a multitude of non-SAML apps with a one-size-fits-all solution. I’ve also implemented SSO like this in the past, so I can speak from experience about how this works and its risks.
The short version of how this works is that the authentication is offloaded to a reverse-proxy, an agent, or a gateway, that sits outside PeopleSoft. Once the authentication process is successfully completed, only then is a connection made to PeopleSoft, and the authenticated user-ID passed to the HTTP header. Then that request has to be trusted by a custom Sign-on PeopleCode.
Aside from the risky firewall configuration, another issue here is that it needs to be scaled carefully for bandwidth because all of the requests will now go through a new server and several new applications to complete the process. Now you have additional hardware, software, and customizations to maintain and patch in addition to your regular PeopleSoft duties.
Why a Native SAML/ADFS Handler is Best Practice
SSO is critical to help you increase your security posture within your organization while keeping your customers happy, so I don’t want to sound negative, and I’m not trying to put you off on installing an SSO solution in your environment. Instead, I want to make sure you do it correctly and aligned to security best practices.
My advice is to use a solution that natively supports a SAML/ADFS authentication handler and seamlessly and securely passes the token to PeopleSoft built-in authentication without customizations. The term “native” is extremely important here! The lack of native support is a critical issue that plagues custom solutions, creating more hoops to jump through to complete the project.
Fortunately, Appsian delivers the SAML/ADFS integration layer required to connect PeopleSoft, an IdP (Okta, Azure AD, Ping Identity, etc.), and your enterprise Single Sign-On. This solution is natively installed right into the PeopleSoft Internet Architecture (PIA) and does not require the use of proxy servers, agents, or gateways. Furthermore, there are zero customizations, simple configuration with extensive support for SAML/ADFS attributes, user-mapping, and the support and maintenance is offloaded from your team.
There is Beauty in Customization but Comfort in ERP Data Security
Part of PeopleSoft’s beauty and power is that you can customize the system to improve your business processes. However, one thing you shouldn’t take into your own hands is authentication, and indirectly, security. Your IT team, system admins, and developers should spend their time supporting and customizing your system to provide outstanding service to the business units and keeping the system running smoothly. Why add more hardware, software, applications, and customization than necessary?
Request a demo today to learn how Appsian solves the SAML/ADFS integration challenge by providing the only configurable SSO for PeopleSoft.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Customer Story] Collin County, Texas, Uses Appsian’s MFA Solution to Improve PeopleSoft Security
Collin County, like all counties in Texas, is considered an extension of state government. Located just north of Dallas, Collin County (the County) provides various government services to its more than 1,000,000 residents. The County’s security team is responsible for enabling secure yet convenient access to appropriate information and services to their on-premise installation of PeopleSoft. Unfortunately, as is often the case with legacy, on-premise PeopleSoft installations, convenient access can lead to security gaps.
What Challenges Made Collin County Search for A PeopleSoft MFA Solution?
The security team at Collin County was observing vulnerabilities in their network regarding potentially unknown people accessing bank account routing numbers. These security gaps made their network prone to phishing attacks by external hackers who could access their network through compromised employee credentials. The attackers also could change the bank account numbers on the direct deposit page so every time the payroll ran, they could deposit the employee paychecks into offshore accounts. Collin County wanted to improve their PeopleSoft data security posture and reached out to Appsian Security to equip them with an MFA solution that could seamlessly integrate into their existing applications without additional servers or customizations.
Collin County Plugged Their Security Gaps with an Adaptive MFA Solution
Following a strategic decision by their Chief Information Security Officer to strengthen data security and protect their network from phishing attacks, the IT leaders at Collin County set out to upgrade and modernize their HCM applications with advanced features to improve data security and block external threats. Using the Appsian Security Platform (ASP), they deployed multi-factor authentication along with logging & analytics to achieve the desired results.
Appsian’s adaptive MFA solution seamlessly integrated with Collin County’s HCM applications without causing additional friction for the users. The County deployed multi-factor authentication to challenge users to reconfirm identity at the page/component level and secured administrative access to PeopleSoft by requiring MFA from everywhere, including in-house. They also secured remote access for banking transactions and improved employees’ payroll data security by successfully detecting and blocking external threats. In addition to multi-factor authentication, Collin County was able to secure sensitive information and PII in nonproduction environments, such as dev, test, and train, by leveraging ASP’s data masking functionality.
End-to-End PeopleSoft Data Security and Compliance with the Appsian Security Platform
Appsian’s PeopleSoft customer base includes multiple state governments and local municipalities, like Collin County, looking for a single platform to strengthen Identity and Access Management, Data Security, and Compliance, including:
- Native SAML/ADFS Compatibility And PeopleSoft MFA Integration– Integrating single sign-on and multi-factor authentication natively with PeopleSoft and your identity provider improves security and convenience. Integrated MFA also enables step-up authentication, so users can be forced to re-authenticate when accessing highly sensitive transactions.
- Contextual Access Control For Greater Security – Reduce the attack surface with a dynamic rules engine that applies the contextual variables of a user’s access and defines privileges in real-time. Implement least privilege to limit access to modules/transactions, dynamically mask sensitive data, enforce step-up MFA, and more.
- Real-Time Analytics For Improved Response Times – Enhanced PeopleSoft logging capabilities capture all user activity at the field, page, and component levels and combines them with contextual user data. Real-time visualized dashboards allow you to quickly spot suspicious activity and drill down to root out issues.
Contact Appsian’s PeopleSoft experts today to learn how the Appsian Security Platform can help you establish an MFA solution and a strong ERP data security posture.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
[Podcast] PeopleSoft Access Security
Appsian’s Executive Director for Security Solutions, Greg Wendt, appears in the latest episode of IAM Pulse, a podcast from BIO-key International that discusses all things identity access management.
In this episode, Greg joins host Kimberly Johnson, BIO-key’s VP of Product Marketing, and Greg Browinski, Principal Software Developer at BIO-key International, to talk about making sure PeopleSoft is not isolated from your IAM strategy but instead seamlessly integrated into it.
Listen to the full episode here:
Episode Summary:
Most organizations are running hundreds, if not thousands of applications, with some running the critical operations of the business. This is the case with Oracle PeopleSoft, which runs inventory, financial services, and campus solutions for universities, colleges, and other institutions. However, it can be complicated when it comes to securing this application and break the mold of a company’s IAM strategy. Greg Wendt, Appsian’s Executive Director for Security Solutions, joins the podcast to discuss how to involve PeopleSoft with an IAM strategy.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
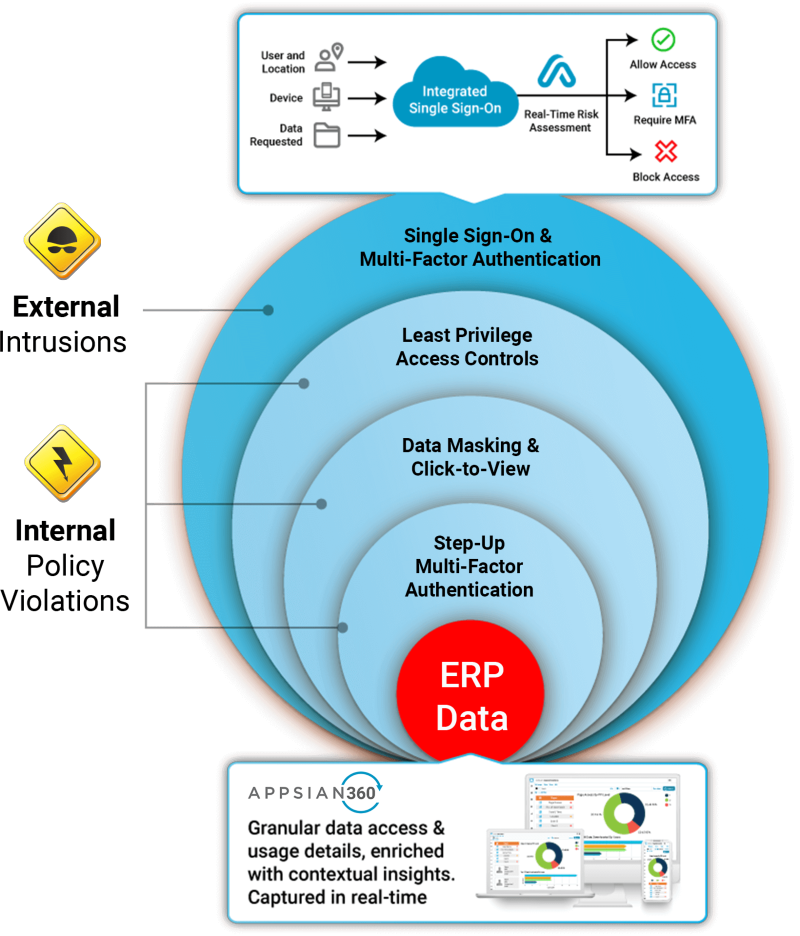
Modernize PeopleSoft Security with Defense in Depth
As work-from-home continues into 2021 indefinitely and the reality of this increased risk becomes clearer, organizations should heavily prioritize the modernization of their existing business applications – especially legacy ERP applications like PeopleSoft. Mainly because native user authentication, governance, data privacy and visibility features can leave an organization open to a myriad of risks. This has opened the door to organizations scoping a defense in depth strategy.
When you hear the term defense in depth, you typically think about traditional information security measures like network security controls, antivirus protection, database monitoring, and more. IT and security teams realized that multiple layers of security are necessary across the enterprise because cybercriminals will find vulnerabilities somewhere. Sadly, some of the most costly vulnerabilities for organizations using PeopleSoft ERP applications have proven to be the users themselves (employees, 3rd party vendors, students, etc.) It’s no secret that making these applications available on the open internet has introduced risk, so we frequently get the question, “how can I apply defense in depth to my PeopleSoft users?”
Step 1: Integrate your Identity & Access Management
This would be integrating your single sign-on and multi-factor authentication natively with PeopleSoft and your identity provider. Using proxy servers or customizing PeopleSoft poses their own risks and complexity, which is why using a native SAML handler (like Appsian) is a best practice. This minimizes the possibility of corruption, and a configurable solution(s) will scale much more effectively.
Integration of multi-factor authentication also enables stepped-up authentication, so users can be forced to re-authenticate once they have already passed the login screen. This should be applied to highly sensitive transactions like editing a direct deposit account number, accessing compensation data, or running a report containing employee PII.
Step 2: Apply Dynamic Authorization in Accordance with the Principle of Least Privilege
Controlling data access for high privilege PeopleSoft users can be challenging because native authorization is basically “all or nothing.” Limiting access to superfluous data or limiting access based on location/device/etc. is simply not an option. Leaving the door open to enormous risk. We have discussed time and time again that the context of access often defines risk, and this is never more true when users can access the system remotely.
Using a dynamic rules engine, Appsian can take the contextual variables of a user’s access and define privileges in real-time. Thus, mitigating risk. Don’t think a user needs access to compensation data from an unmanaged device or certain location? Want to limit the access granted to users or 3rd party vendors at certain hours of the day? Then dynamic authorization is the solution for managing that risk.
Step 3: Mask Sensitive Data Fields (Partial, Full, or Click-to-View)
This is data privacy 101, and as regulations like GDPR and CCPA become the norm (with wider federal guidelines likely coming soon), masking sensitive data is table stakes. After all, with PeopleSoft systems housing a wide range of PII, much of which belongs to past or prospective users (not just current employees), there is a treasure trove of personal data that comes with a far greater holding cost than you might realize. Masking data at the UI level at least ensures that those accessing the applications either in an authorized or unauthorized manner do not have needless access to valuable data through various pages, reports, or queries.
Step 4: Monitor Data Access & Usage
Monitoring the data users are accessing is not possible in PeopleSoft without enhancing logging and analytics capabilities. Having greater visibility cannot be overstated, and having a direct view of how data is accessed is one of the most valuable pieces of defense in depth. After all, in a sea of every day, authorized activity – how likely are you to detect the subtle hints of unauthorized activity? Phishing and privilege misuse are the main enemies of any data loss prevention strategy. The best way to detect and respond to unauthorized activity is through an analytics platform specifically designed for ERP applications, like Appsian360.
Step 5: Contact Appsian
To learn more about how you can apply Defense in Depth to PeopleSoft, contact us at info@appsian.com.
Figure 1: Prevent external and internal threats with defense in depth from Appsian.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives









