3 Reasons Why You Need a Comprehensive SAP Role Audit Before a S/4HANA Migration
As SAP ECC customers prepare for their migration to S/4HANA, they are assessing the pros and cons of this transition in terms of cost, compliance, and data security. A critical step in an S/4HANA migration involves a thorough SAP audit of the existing roles and authorizations and optimizing license spends for the current users. Organizations need to consider three key factors during a complete SAP audit for better role management before an SAP S/4HANA migration.
SAP Role Audits Can Optimize Your License Spend
Many organizations still view their SAP licensing as a black box. They are ready to spend millions of dollars on SAP without understanding which licenses are being consumed or which licenses are required for each user. A common mistake many organizations make without realizing it is misclassifying users due to the lack of visibility into the usage of each employee.
A comprehensive role audit in SAP can help classify all users, accounts, and roles and eliminate those not in use, including the following best practices for optimizing license spend before the SAP S/4HANA migration:
Combine Users Between SAP Systems
Often, a single license is enough to access multiple SAP applications. Combining the same user across multiple applications frees up licenses that can be allocated to other users—preventing companies from paying double the amount.
Remove Inactive or Dormant Users
Certain users access the system only a few times a year, yet they are assigned Professional or Limited Professional License types. Since many corporations do not have visibility into the actual usage data for each role, account, or user, it is difficult to identify the inactive roles. By eliminating inactive and dormant users, organizations will be able to reallocate licenses to new users immediately, providing instant savings.
Classify All Users and Roles
Most SAP users utilize only a fraction of their allocated authorizations. Focusing on the actual usage of data based on the users’ roles ensures that companies will never be under or over licensed. In addition, by classifying all users, organizations can avoid the additional costs of Professional Licenses (used only by unclassified users).
SAP Role Audits Ensure Data Security Via Dynamic Access Controls
S/4HANA migration often opens up the “crown jewels” data to the security risks of the mobile world because the network firewall no longer protects it. You need to know what type of data is being exposed to your external users. That determines how you define the roles and how data is taken from the application and delivered to the users.
This requires applying protection to the user interface layer in terms of defining how you want the data to be viewed by different personas. Organizations conducting SAP audits need to enable dynamic access controls to gain visibility into:
- Where is a user coming from?
- What data are they trying to access?
- What device are they using?
- Is that device being used by the right person?
- What data are they trying to extract onto their device?
Periodic reviews and audits of the roles ensure that only the correct user having the proper roles can view the sensitive data that is otherwise encrypted or masked. For example, not every HR employee should have the role or access rights to view employees’ payroll data.
SAP Role Audits Are an Opportunity to Verify SoD Compliance
Organizations migrating to S/4HANA need to leverage SAP access controls or security monitoring solutions to perform periodic role and user analysis. The data collected during this audit can also help verify SoD compliance. Segregation of Duties conflicts, especially in financial and procurement transactions, are a significant reason for audit failures. Role audits could be used as an opportunity to collaborate with your organization’s compliance team to ensure that you’re securing your data and adhering to mandatory compliance requirements across your SAP ecosystem.
How Appsian’s ProfileTailor GRC Helps with SAP Role Audits
Migrating to S/4HANA remains a long and complicated process for organizations. The first big step is an exhaustive audit of the new and existing roles to facilitate effective role management in the SAP system. Role management offers access simulation capabilities, enabling administrators and role owners to perform a “what if” analysis at various stages of a role’s life cycle management and support compliant user provisioning. In addition, the system provides mechanisms for role design to reduce SoD conflicts and improve administration efficiency in SAP and other ERP and business applications. This usually includes a mechanism for transporting new or updated role definitions into appropriate application environments.
Appsian Security helps businesses with its ProfileTailor GRC Solution, ensuring cross-platform ERP data security, compliance, and SAP license optimization. It delivers unprecedented visibility of real-time authorization usage, helping companies optimize their spending before migrating to S/4HANA.
Want a secure and seamless transition to S/4HANA without spending a hefty sum on your licenses? Then, download our whitepaper, Critical Steps You Should Take Before Making the Move To S/4HANA, and reach out to schedule a demo with our SAP security experts.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Why Automation is Key to Resolving SoD Conflicts in SAP
Companies using SAP typically have some type of structured governance, risk, and compliance (GRC) strategy to manage their overall governance and enterprise risk management and meet compliance requirements. An essential component of any GRC strategy is detecting and resolving SAP segregation of duties (SoD) conflicts.
SoD weighs heavily on financial management and reporting, especially for public companies or those receiving government funds. When unresolved SOD conflicts appear on audit reports, a company’s compliance with the Sarbanes Oxley Act (SOX) and data privacy regulations like GDPR are negatively impacted.
Spreadsheets: The Traditional Approach to Managing Segregation of Duties
For a long time, companies have relied on spreadsheets to track and maintain roles and authorizations granted to employees. While spreadsheets are great to get started on your compliance program, they can create several hurdles as your organization grows in size and complexity.
- Human Error: No matter how meticulous, humans are prone to making errors, especially when dealing with thousands of rows across multiple sheets and files. Every new change can trigger a cascade of changes which is hard to keep track of manually.
- Low Visibility: In most cases, it’s more than just one person working on the spreadsheet with no visibility into who is editing what and where. With multiple teams/members making changes, the probability of error also increases.
- Reporting Delays: Collating, validating, and analyzing data that is spread across various tabs and files requires a significant amount of man-hours. This results in reporting delays and after-the-fact detection of SoD conflicts.
- Lack of Audit Trails: Simply put, Excel sheets cannot maintain an audit trail. Even if you can track changes, getting into each version of the file to view changes is a long and laborious process.
- Limited Insights: Spreadsheets are static and do not have the ability to cross-reference data to provide actionable insights. Also, manually sifting through large volumes of data makes it difficult to detect behaviors that impact risk.
The reasons mentioned above make it abundantly clear that the spreadsheet method of tracking and resolving SoD violations is slow, inefficient, and error-prone. With regulatory authorities imposing compliance mandates and hefty fines on companies that fail to meet audit requirements, there is an immediate need to update your approach to GRC with tools that are equipped for the job.
Segregation of Duties Conflicts Are Not Static
An increasing number of companies who use SAP are realizing that segregation of duties conflicts are a significant cause of audit failures. This is mainly because SAP authorizations are not static, and neither are SoD violations. As employee roles and duties change over time, it becomes difficult to keep track of authorizations and SoD rules that govern the limits of each role. For example, when a procurement team member who is authorized to approve new vendors retires, this role could be assigned to someone on the team who is authorized to issue purchase orders. This immediately creates a conflict of interest and results in an SoD violation.
In large organizations, such violations happen regularly, and without the tools to detect and resolve them immediately, an audit failure is inevitable. To address this challenge, companies deploy simulation solutions that allow them to see if granting an authorization could cause an SoD conflict. However, these results are generally ignored since most simulation tools do not offer options to resolve the conflict. The reality is that holding up authorizations can directly impact the operational efficiency of the business, which usually wins over compliance requirements in the short term.
Automation is the Key to Resolving SoD Conflicts
To be able to proactively detect and prevent SoD violations, organizations need to go beyond simulation and invest in solutions that can constantly monitor SAP roles and authorizations. In fact, solutions that can go one step further and offer options for resolution will allow administrators to quickly take action without creating further conflicts. Appsian Security ProfileTailor GRC was designed keeping in mind the challenges faced by companies who struggle with meeting compliance due to SoD conflicts. With real-time automated monitoring capabilities, ProfileTailor GRC enables you to immediately detect and resolve SoD violations within a matter of minutes.
Whether you have new employees needing authorizations, current employees changing positions or roles, or someone leaving the organization, ProfileTailor GRC will do the heavy lifting for you and provide you with an ongoing, fully automated, and integrated solution.
Download our white paper Quickly Resolve Segregation of Duties Conflicts to learn how automation can help enable GRC in your organization.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How Appsian Improves SAP Segregation of Duties Violations Management
From stopping fraud, theft, and errors to preventing SOX compliance violations, SAP Segregation of Duties (SoD) plays a lead role in minimizing business risk. Organizations must continuously iterate their internal controls to ensure their SoD strategy is effective; however, we all know this is easier said than done.
What are SoD Violations?
A Segregation of Duties or SoD violation occurs when a user has more control over a particular workflow than needed. For example, if a user can both approve new vendors and release purchase orders, it creates a conflict of interest that could, potentially, lead to fraud. The primary goal of implementing SoD is to, first, prevent users from gaining authorizations that create conflict and, second, to detect existing user authorizations that are in violation of organisational policies and/or compliance regulations.
Finite Resources & Manual Processes Can Only Address So Much
With existing capabilities, audit preparation and reporting are manually intensive processes that deliver an outdated snapshot of risk. Time and effort are wasted investigating immaterial events (i.e., false-positives, non-financial activity) because audit logs miss relevant details. Furthermore, manual analysis can be prone to errors, unscalable, and increasingly costly.
Due to resource-intensive audit processes, most organizations can only review a fraction of their SoD audit findings. This limited sample scope, typically between 3-8%, leaves the vast majority of risk unaddressed. While the sample may indicate control effectiveness, significant material risks may go undetected, and confidence will be curbed.
Leveraging Technology to Reduce Your SAP SoD Risk Exposure
Existing SAP SoD audit logs will show transaction activity but lack the data-level granularity to identify and filter out false-positive SoD violations. Manual investigation and correlation must be performed to do this – adding overhead, slowing the reporting process, and making it more difficult to prove compliance.
The bottleneck stems from technology and dictates unscalable processes. One approach to overcome this challenge is to adopt data-centric logging, which provides relevant details beyond roles and transactions – enabling customers to automate the majority of manual investigation and correlation efforts. From here, organizations can shift their valuable human resources towards remedial activities to further reduce SoD risks.
How Appsian Improves SAP Segregation of Duties Violations Management
Delivering data-centric logs paired with contextual information, Appsian360 provides visibility into SoD violations with far greater detail than what is possible with existing transaction-level audit logs. This additional information enables customers to eliminate false-positives automatically, view actual SoD violations, and prioritize events based on relevant details (e.g., dollar amount, time/location performed, etc.)
Leverage data-centric visibility to streamline SAP Segregation of Duties:
- Uncover 100% of SoD violations with data-centric continuous controls monitoring.
- Capture actionable details that would previously require manual investigation.
- Gain an always current view of SoD risks with continuous audit capabilities.
- Prioritize investigation & remediation activity by eliminating wasted effort on immaterial events.
- Simplify proving compliance with granular visibility and contextual information that is missing from existing audit logs.
- Get a Demo of Appsian360 and See for Yourself
As the burden of SAP SoD compliance grows, organizations must look towards technology to help automate tedious manual processes and strengthen internal controls. At Appsian, we’ve built our solutions with this need in mind, delivering a platform that enables SAP customers to do more with less. Contact us today for a demo, and let’s explore how we can help your organization streamline SAP segregation of duties.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Improve SAP Access Policy Management During These Turbulent Times – and Beyond
In these less than ordinary times, organizations are dealing with disruption at a frequency higher than ever before. An unfortunate side-effect of this COVID crisis has been its impact on employees. Whether furloughed, laid off, or set to take on broader responsibilities, change is happening. And naturally, these changes must be reflected in your ERP applications’ access policy management.
The uptick in user provisioning is placing additional pressure on SAP security and IAM teams, already burdened with securing remote access to applications for people working from home. These days, you have to wonder if IT professionals are feeling like they’re chasing something they can’t keep up with. And that leads to problems.
Joiners, Movers, and Leavers
The user provisioning process typically encompasses three phases: joiners, movers, and leavers. In short, they are three separate scenarios – when employees are onboarded, when they switch positions/departments internally, and when employees leave the organization. Given COVID, leaving the organization could mean either termination or furlough.
If overburdened IT and security teams cannot address provisioning promptly, organizations are leaving themselves open to an onslaught of risk in times where cyber-attacks are peaking and employees are already feeling stressed out.
Thanks to an enlarged threat surface from remote access, a compromised account can cause considerable damage before it is detected. Excessive privileges only multiply this risk. Alternatively, strained and disgruntled employees with excessive privileges may be tempted by fraud, especially in cases where segregation of duties (SoD) should be in play. If an employee was given extra responsibilities that necessitated new roles, potential conflicts might be overlooked.
Three Tips for Improving SAP Access Policy Management
Setting the roles is only one step. You don’t want to give everybody the same kind of visibility or access to data, depending on their role. This is a great time to invest in data security technology and establish more granular access policies. Here are three tips for improving your SAP access policy management:
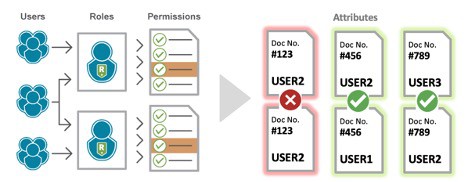
1: Leverage Attribute-Based Access Controls (ABAC) to Simplify User Provisioning
Organizations with similar roles spanning multiple business units turn to role derivatives to ensure access is segmented appropriately. While effective from a control perspective, managing these roles can prove burdensome as the number of role derivatives multiply with each branch-off.
For example, a manufacturing organization has 50 functional roles shared by users across 10 different plants. Using role derivatives, they would end up managing 500 different roles to ensure access is segregated appropriately. The sheer scale can be overwhelming to your SAP security team to begin with – and now we’re adding in all the joiners, movers, and leavers from COVID-induced workforce changes.
The purpose of roles is to be scalable! We want access policies that are one-to-many, not one-to-one. To gain back simplicity and lighten the load on your IAM teams, organizations can extend their existing role-based access control (RBAC) model with attribute-based access controls (ABAC). ABAC allows you to easily bring fine-grained “attributes” into your authorization decisions. In the example above, one could go from managing 500 role derivatives down to 50 roles and 1 supplemental ABAC policy that can consider the differing factor, a user’s assigned plant code, to automatically segregate their access appropriately.
2: Reduce Your Attack Surface with Fine-Grained Entitlements
The Principle of Least Privilege is a crucial tenet in information security. The goal is to minimize risk by providing users with the minimum level of access needed to perform a task at hand. This is the purpose of existing role-based access controls – e.g., an HR manager should not have access to finance transactions because it is out of their scope. However, this does nothing to protect data within their scope. Should the HR manager have access to social security numbers or compensation data at all times? After hours? Remote? The answer is likely, no.
Organizations can reduce their amount of accepted risk by applying granular business policies and access controls to strengthen data-level and transaction-level security. Leveraging ABAC, you can enforce risk-aware controls to place limitations on what users can access within your application, from where, when, how they can access, and what they can do with data. ABAC provides an additional level of security by incorporating additional context like geolocation, time of day, and IP address. This ensures appropriate user access and prevents users from having more access than they need. Want sensitive data masked when access is outside your network? Done. Want to block high-risk transactions after hours? Easy.
3: Manage the Identity Lifecycle with User Activity Monitoring
Organizations should always engage in some kind of user activity monitoring, regardless of the number of joiners, movers, and leavers they’re dealing with. But this monitoring must extend beyond time-consuming and potentially expensive manual audits. You want to make sure the access control policies you’ve established are working and that you’re watching for anomalies. Some user activity to consider monitoring includes:
- Identifying high-privilege user activity and critical transactions while closely monitoring and auditing on a regular basis
- Continuously monitoring access across peer group activity for visibility into who changed what in regard to roles and permissions
- Setting risk-aware alerts such as location of user, device accessing network, etc. This monitoring is vital for streamlining threat detection and alleviating the manual process typically required for threat response
Assign Ownership and Responsibility Over User Provisioning
While you’re monitoring user activity, don’t forget to put some eyes on your IT and security teams. You’ll want to assign ownership and responsibility to whoever responds to access requests and reviews temporary team member access. Keep good records as to why approvals are made or changed. You’ll want to approach this in a way that is easily audited. (Tip: email is not that process).
Conclusion
There are many moving parts and people that IT staff and security teams must manage. Leveraging tools that can improve an organization’s SAP access policy management will go a long way towards protecting important data and easing the burden on stressed IT and security teams.
Schedule a demonstration today and learn how Appsian can mitigate SAP business risks with ABAC and User Activity Monitoring.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How to Streamline the SAP Segregation of Duties Exception Process Using Attribute-Based Access Controls
Secure, compliant, and efficient business processes are critical to enterprise operations. In SAP, Segregation of Duties (SoD) is a key principle in making this possible.
What happens when an SoD exception is necessary?
Often times a user will need to be granted roles and privileges that pose a conflict of interest. It could be that an employee is part of a small department, or that a security clearance precludes others from involvement. Whatever the reason, this user needs the ability to handle multiple steps in a business process – and an exception is made.
Here’s where things can get tricky. Once an SoD exception is made, your standard preventive controls are no longer effective. This is one of the major shortfalls of SAP’s static, role-based access controls.
Shifting from a preventive approach to a detective approach…
… you must now gather access logs, filter out false-positives, and finally, send to the appropriate control owner to review and sign-off. Besides the additional overhead of manual reviews and approvals, detective controls create room for human error and increase the dwell time before red flags are caught.
So why are current SAP SoD Controls limited?
Without the logic ability to decipher potential violations from actual violations, preventive controls are a non-starter. Your (preventive) SAP access controls determine authorizations based on two things: 1.) a user’s role and 2.) the role’s associated permissions (think transactions.) While this works in the vast majority of cases, enforcing SoD requires controls with more granularity.
Let’s take a look at what an actual SoD violation entails
The whole objective of SoD is to avoid conflicts of interest in your business processes. Although, conflicting transactions do not necessarily pose a conflict of interest, unless the subject is the same.
For example, a user performs the transactions to create and approve multiple purchase orders. Looking at the transactions themselves, this activity has the potential for violations. Looking deeper into the PO details, you may see that the user never created and approved the same PO – therefore no violation was made.
SAP can show you 1.) the user and role, and 2.) the transactions performed, but is missing the 3rd component: the field-level values in the PO itself. This lack of visibility into attributes beyond roles and permissions is what makes preventive controls a non-starter and clutters SoD audit logs with false-positives when exceptions have been made.
The Solution? Enforcing SoD Policy with Attribute-Based Access Controls
Attribute-Based Access Controls (ABAC) enable the use of “attributes” in authorization decisions. These attributes can be anything from user details such as role, department, nationality, or even a user’s security clearance level. Additionally, access context such as IP address, location, time, device and transaction history can be considered. And most importantly for SoD, data attributes can now be used in authorization logic. This means that field-level values within SAP can be used to determine whether to block or allow a transaction, and these details can further be used in reporting activities.
In the Purchase Order example above, data attributes can be used to identify whether a user performed the first transaction and make the correlation that performing the second transaction would result in a violation.
Combining SAP’s role-based access controls (RBAC) with an attribute-based access control (ABAC) solution enables granular control and visibility that delivers a wide range of business benefits.
Newfound Flexibility in SoD Exception Scenarios – RBAC + ABAC Hybrid Approach
The RBAC + ABAC hybrid approach opens the possibility to apply preventive controls in SoD exception scenarios. By doing so, you can offer users the flexibility an exception provides while still preventing any actual violations from happening.
Together, this hybrid approach (RBAC + ABAC) enables a dynamic SoD model that prevents violations while still allowing the flexibility of conflicting roles to be assigned (when necessary) and reinforces role-based policy to mitigate over-provisioning.
RBAC + ABAC Hybrid Approach Using Appsian
Appsian adds an additional authorization layer to SAP GRC Access Control that correlates user, data and transaction attributes, along with identified SoD conflicts, to block conflicting transactions at runtime.
Contact Us to learn more about how a hybrid access control approach can strengthen Segregation of Duties (SoD) at your organization.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives