According to a recent Shred-It survey, both senior leaders and employees indicated data breaches doubling in frequency in the last few years. Consequently, these same groups also reported modest but still peculiar decreases in cybersecurity training commonly used to identify tactics like phishing, ransomware, or other malicious software. Senior leaders saw a 6% drop, and employees saw a 7% drop from 2019-2020. While not eye-popping numbers by themselves, it begs the question – if data breaches are going up, why is cybersecurity training going down?
You could argue that a top theme of 2020 would be the dramatic rise in data breaches, so it’s worth wondering if a downward trend in training is likely to continue, or will it reverse course in 2021?
Cybersecurity Training for Employees May No Longer Be Relevant?
This is a controversial and over-simplified statement, but the downward trends point to this attitude within organizations. If cyberattacks are evolving in sophistication each day, then how can organizations keep up? At what point do you accept the fact that attacks are likely to be successful, and you need to invest your resources in risk management and mitigation? The truth is, information security professionals are constantly playing behind the 8-ball when it comes to combatting employee-targeted cybercrime. Spoofed landing pages and emails that mimic corporate branding can be created in a matter of minutes – while LinkedIn, along with countless databases, have made it simple to discover and exploit org charts. If cybercriminals are always one step ahead, is cybersecurity training constantly obsolete?
Is Employee-Targeted Cybercrime Becoming Too Hard for Employees to Spot?
As the head of a department myself, who reports directly to the CEO, I cannot begin to tell you how many emails I’ve received “from” my CEO, disguised to send money, reports, or some information that a hacker would use maliciously. It’s not magic. The hacker found my CEO, worked their way backward to assume who the direct reports were, created a perfect replica of my company’s email signature, sent it around, and hoped for the best! The only reason it didn’t work is because I scrutinized the nature of the request – not the email used to make the request. The email was flawless.
Let’s apply this enterprise-wide. Heading into end-of-year, countless employees will be asked up update information in their ERP applications. All for many reasons – benefits open enrollment, updating personal information so tax documents or bonuses can be received. Spoofed “update your password” emails and landing pages that are designed to steal login credentials are the #1 cause of identity theft and payroll diversion. Why are they so effective? Because if you have the ERP login credential, you have the power! Primarily relying on a password security model means employees must correctly scrutinize those spoofed emails and landing pages, then choose NOT to comply with what this spoofed “corporate email” is telling them to do. How effective do you think that will be throughout an entire organization?
It is challenging to teach scrutiny, but organizations are trying. The lesson always is – never open attachments from outside email addresses, never send personal information, etc. However, in the age of remote work and ubiquitous mobile device usage, relying on this level of scrutiny is extremely difficult. And the hackers know this! Detecting spoofed emails and landing pages is tough enough on a desktop, but it’s extremely hard on a mobile device.
What’s a More Effective Way of Preventing Cybercrime?
Simple. Using software to analyze email links and attachments (which most companies are already doing) and making the data that the hackers want more difficult to obtain (ex. employee PII from ERP applications.) Information security teams use these solutions to fail-proof an employee’s lack of scrutiny. As these solutions become more sophisticated, it makes sense for these to be your primary areas of protection. Leaving good ole’ employee training in the dust.
Is Cybersecurity Training for Employees Still Relevant?
Short answer, yes! Employees should always be doing their part to protect their personal data, along with business data. However, the inverse trend in data breaches and training is simply a reflection of a re-allocation of resources. Or, as my dad would say, “the juice is not worth the squeeze.” Training a workforce is extremely complicated and expensive. As technology evolves to the point where it can do the scrutinizing for employees, we’re likely to see the downward trend in training continue.
How Can I Protect Legacy ERP Data Since Data Breaches are Going Up?
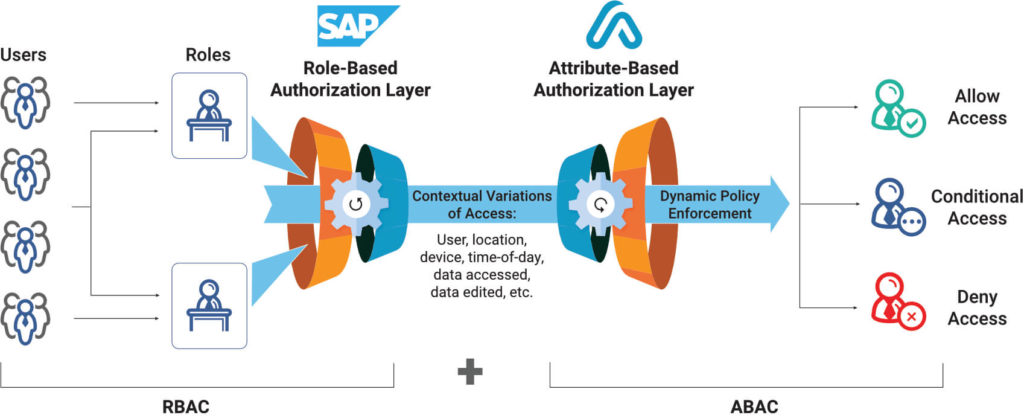
Another short answer, invest in ERP data security! Like I discussed above, solutions that provide risk-aware controls reinforce authentication protocols (ex. multi-factor authentication) and enable data access & usage monitoring are available. However, organizations must be aware that not all applications are created equally when it comes to control and visibility.
Legacy ERP applications like SAP ECC, PeopleSoft, and Oracle EBS require additional sophisticated solutions to enable control and visibility because their native security features have an antiquated focus. Their native security features rely solely on usernames and passwords, static governance policies (role-based access controls), and system logging designed to troubleshoot application errors – not monitor data access.
This is where Appsian has helped hundreds of legacy ERP customers – and can help you as well. Contact us today, and we’ll show you how you can enable a sophisticated data security model (for legacy ERP data) in a matter of weeks!
And whether you decide to do more or less cybersecurity training for employees, know that Appsian is here to protect your data no matter what tactics malicious attackers try to use!