When it Comes to ERP Data Security, Context (of Access) Matters – Appsian360 Can Help!
Organizations using traditional, on-premise ERP applications like SAP ECC and Oracle PeopleSoft are facing a rapidly changing reality around the collection, storage, and usage of data. Aside from the growing number of compliance regulations they need to follow, such as GDRP, CCPA, and others, they face critical visibility gaps related (explicitly) to understanding ERP data access & usage. Especially at a fine-grained level.
This lack of visibility is exacerbated by organizations enabling remote and mobile access to their users, exposing them to a myriad of data security and compliance threats like hacking (phishing), along with fraud and theft from internal users. All of which result in the loss of millions of dollars each year.
Fortunately, ERP applications that were once considered a “black box” can now be enhanced with the most sophisticated logging and analytics technology available on the market. Introducing Appsian360, the first and only data access and usage analytics platform for SAP and PeopleSoft.
Why Context of User Access and Data Usage Matters
Far too often, user behavior is a mystery, resulting in security, fraud, theft, and business policy violations. Specifically, a lack of detailed insights regarding how, when, and by whom transactions and data fields are being accessed.
As they exist today, legacy on-premise SAP and PeopleSoft systems simply do not provide organizations the granular visibility and context of user access and data usage they need in real-time to make proactive and strategic decisions.
“For years, organizations have been operating with limited visibility, and current threats to ERP data have made this status quo completely intolerable,” said Piyush Pandey, CEO of Appsian. “Appsian360 is about knowing who is doing what – at a very granular level.”
With Appsian360, security and compliance leaders can drill into specific data access and know exactly who is doing what, where, and why. With that level of in-depth, contextual information, any red flag incidents can undergo a rapid response plan.
“The beauty of Appsian360 is it’s a comprehensive solution that provides actionable insights,” added Pandey. “We know that forensic investigations and time to mitigation costs organizations countless amounts of money – and we’re pleased that Appsian360 can alleviate much of this burden.”
Appsian360 for SAP and PeopleSoft
Appsian360 installs into your ERP web server and does not require any additional customizations. There are zero noticeable effects on application performance. Here’s a high-level look at what Appsian360 can do for you.
Detect Security Threats in Real-Time: Appsian360 proactively alerts you to security threats like hacking, phishing, misuse of privileged accounts, and many more. You can quickly receive the information required to fully enable forensic investigations.
Uncover Hidden Business Risks: Appsian360 helps you detect and respond to fraud, theft, and errors by employees and third parties (vendors, consultants, etc.). Companies can maintain a complete view of sensitive business transactions, and what (specific) users are doing.
Monitor Employee Productivity: Appsian360 helps you maintain oversight as users process and execute business transactions. You can use these insights to ensure efficient staffing and identify potential bottlenecks in critical HR, payroll, and finance activities.
Understand Data Access & Usage with More Clarity Than Ever Before
Organizations can no longer rely on having a lot of data. They need to start triangulating and developing context around the data they’re getting and how it’s being used. Appsian360 provides real-time data access and usage visibility previously unavailable to SAP and Oracle ERP customers.
To see how data security and compliance threats that were once considered “the price of doing business” are no match for the watchful eye of Appsian360, join us for a virtual demonstration on Thursday, August 13. You can register here: https://www.appsian.com/visibilty-using-appsian360/.
Contact us today for a personalized demo and find out how Appsian360 can fill critical visibility gaps for your organization.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
The RECON Bug Highlights SAP Customers’ Need for Fine-Grained Control and Visibility (Not Just Security Patches)
A critical SAP vulnerability (CVE-2020-6287 or RECON) was recently discovered by Onapsis that gives attackers TOTAL control of vulnerable business applications. It allows hackers to gain unauthenticated access to SAP and then create new user accounts with admin (superuser) privileges. With these privileges, a malicious attacker can do limitless amounts of damage, including stealing data, changing bank account numbers, fully sabotaging systems, and more.
RECON Shares Similarities to a Familiar Foe – 10KBLAZE
The RECON vulnerability puts the confidentiality, integrity, and availability of SAP ERP data and processes at risk, which is very similar to the 10KBLAZE exploit from 2019. What do these two exploits have in common? Simple, they are leveraging a lack of visibility and control to be successful. There is a reason that these exploits focus on the creation of admin accounts – because once you’re an admin (legitimate or not), you have the keys to the castle.
The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators of SAP products to:
- Analyze systems for malicious or excessive user authorizations.
- Monitor systems for indicators of compromised accounts resulting from the exploitation of vulnerabilities.
- Monitor systems for suspicious user behavior, including both privileged and non-privileged users.
- Apply threat intelligence on new vulnerabilities to improve the security posture against advanced targeted attacks.
- Define comprehensive security baselines for systems and continuously monitor for compliance violations and remediate detected deviations.
The key recommendations align to the need for monitoring – monitoring systems, monitoring transactions, monitoring the creation of accounts, and (most importantly) monitoring data access and usage. This is where many SAP ERP customers will struggle as attaining fine-grained controls and visibility are complex, even prohibitive at times, with native functionality. This is precisely where Appsian can help.
A Second Layer of Defense: Fine-Grained Control and Visibility
RECON and 10KBLAZE highlight that a single, static layer of security within SAP is inadequate to combat modern-day threats. Appsian enables SAP ERP customers to layer their defenses using a comprehensive suite of fine-grained, risk-aware access controls, and continuous monitoring of data access and usage.
Here are Appsian’s recommendations to minimize your attack surface and the risks posed by RECON – and future vulnerabilities like it (in addition to recommended security patches.)
Attribute-Based Access Controls (ABAC) Are Essential in a Dynamic Environment
RECON and 10KBLAZE take advantage of vulnerabilities in the open, internet-facing components of SAP (think remote access). The Appsian Security Platform (ASP) uses attribute-based access controls (ABAC) to implement data-centric, “risk-aware” controls. ABAC prevents specific transactions like user provisioning when access originates from untrusted IP addresses (or IP addresses outside your whitelist), certain geographic locations, outside work hours, mobile devices, and many other contextual attributes. Bottom line – Appsian can stop the creation of a user account (or changes in privileges) if access is coming from outside the corporate network. Fine-grained policies can be implemented to block high-risk activity, such as those matching the RECON attack patterns.
Visibility into Data Access and Usage is Essential for Combatting Configuration Gaps
Both RECON and 10KBLAZE center around the unauthorized creation of high privileged user accounts. Appsian360, the latest real-time analytics solution by Appsian, captures and visualizes data access and usage, which is essential for monitoring user provisioning activity like user creation/deletion and role/profile changes. Appsian360 can detect and alert organizations at the point of initial account creation, minimizing the damage by reducing how long a threat goes undetected.
Appsian360 can also detect suspicious transaction activity if the compromised and illegitimate accounts are not addressed at the point of creation. Furthermore, this creates an audit trail that acts independently from existing SAP logs and can expedite breach forensics activities.
Prepare Yourself for the Next Critical SAP Vulnerability – Layer Your Defenses (While and After you Patch Your Applications)
RECON isn’t the first critical vulnerability to affect SAP, nor will it be the last. While there are security patches available to keep their ERP systems safe, these can take time (and resources) to implement, which results in significant downtime of production systems. Furthermore, the time to apply the patches depends on the complexity and the components involved. By all means, stay up to date on system updates, but bugs like RECON and 10KBLAZE serve as a reminder that patches aren’t enough to protect critical SAP data.
Talk to the SAP Security Experts at Appsian today to discuss how your organization can address the risks posed by RECON and other vulnerabilities.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
SAP RECON Vulnerability Puts Thousands of ERP Customers at Critical Risk
A critical SAP vulnerability (CVE-2020-6287 or RECON) was recently discovered by Onapsis that gives attackers TOTAL control of vulnerable business applications. The RECON vulnerability allows hackers to penetrate SAP systems and create new users with administrative privileges, allowing them to manage (read/modify/delete) every record/file/report in the system.
The RECON bug is one of those rare vulnerabilities that received a maximum of 10 out of 10 rating on the CVSSv3 vulnerability severity scale, so it is crucial that organizations move quickly to apply patches.
Remote and unauthenticated attackers can exploit the vulnerability to create a new SAP admin user, bypassing access and authorization controls and gaining full control of the SAP system. Exploitation will impact the confidentiality, integrity, and availability of SAP applications. With an admin-level user account at their disposal, an attacker can:
- Steal personal identifiable information (PII) from employees, customers, and suppliers
- Read, modify or delete financial records
- Change banking details (account number, IBAN number, etc.)
- Administer purchasing processes
- Disrupt the operation of the system by corrupting data or shutting it down completely
- Perform unrestricted actions through operating system command execution
- Delete or modify traces, logs and other files
The RECON Attack Path
The RECON vulnerability is easy to exploit and resides in the LM Configuration Wizard component of the SAP NetWeaver Application Server (AS) JAVA. The LM Configuration Wizard of SAP NetWeaver AS JAVA does not perform an authentication check, allowing an attacker without prior authentication to execute configuration tasks to perform critical actions against the SAP Java system, including the ability to create an administrative user. This compromises the Confidentiality, Integrity, and Availability of the system.
The vulnerability not only compromises the security of the NetWeaver Java applications but can also be used to exfiltrate credentials to an ABAP system through the ABAP secure storage and potentially lead to the exposure of ERP data-sensitive PII and financial information.
SAP Guidance: Apply the Patch or Enable a Workaround
The critical nature of this vulnerability caused the Cybersecurity and Infrastructure Security Agency (CISA) to strongly recommend organizations immediately apply patches, as noted in SAP Security Note #2934135.
If you cannot apply the patch, then at least disable the tc~lm~ctc~cul~startup_app application, as described in SAP Security Note 2939665. Note 2939665 is a workaround and a defense-in-depth, but not a solution.
Further Risk Mitigation Measures
Being up to date on the patches will help mitigate the vulnerability. Still, because of the number of security patches released in recent years, several customers are behind on these as the application of these patches requires downtime of the production systems. Moreover, the time to apply the patches depends on the complexity and the components involved. It can require a significant amount of time and effort, especially if the systems are a couple of patches behind.
All this ends up increasing the risk and the timeframe for which the systems are exposed. Having application security in the form of multi-factor authentication or additional policy-based controls and logging will help mitigate the risks and control sensitive data exposure in mission-critical systems.
Talk to the SAP Security Experts at Appsian today to discuss how your organization can address the risks posed by RECON and other vulnerabilities.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Appsian Releases Report Revealing Executive Perspective on SAP Business Risks and Controls
Every organization using SAP ERP applications faces the unique challenge of maintaining a strong security posture while enabling productive business processes. Throw in the uncertainty of today’s rapidly changing environment, and you can bet that IT professionals and business stakeholders are facing misalignment between IT controls and business rules and objectives.
To discover how organizations are evolving their security and risk management practices, Appsian commissioned a survey of nearly 200 senior stakeholders using SAP applications through an independent market research firm. We compiled the results of our survey into the SAP Security Report: Executive Perspective on SAP Business Risk Management.
We found that this rapid state of change in today’s environment has brought about a new normal for acceptable risk in SAP – but not by choice. While some organizations are adopting new processes and technology to address risk, legacy strategies are holding back many in their path towards efficiently managing ERP data risks.
We also uncovered four key takeaways from the respondents:
1. Business Process Risks Are Slipping Through the Cracks
Executive confidence is wavering in an organization’s ability to detect business risks from fraud, theft, and human error. While concern is generally high, a lack of consistent visibility into these business processes highlights a gap that many have yet to address.
2. IT Leaders Are Concerned About Excessive User Privileges
Excessive user privileges continue to be a top concern of leadership – and for good reason. Users have the keys to your kingdom, and with this, pose a heightened risk if their accounts are compromised or if they engage in malicious activity.
3. Misalignment is Hurting Confidence in SAP Security
Tight alignment between SAP security controls and business goals and objectives is paramount to secure, compliant, and efficient business processes. However, many respondents signal that the two are not aligned effectively.
4. Limited Visibility & Complex Controls Are Hindering Progress
Organizations are facing the limitations of their existing technology and processes. Solving this will require a new approach to overcome complexities in controls and limited visibility into their business-critical applications.
Want to gain a better understanding of how organizations are evolving their ERP security and risk management practices? Curious about the kinds of risks organizations are most concerned about, and how they view and prioritize user and system visibility, access control, oversight, and accountability?
Download your free copy of the SAP Security Report today and take a deeper dive into these findings.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
CCPA Enforcement Is on Track to Start July 1, 2020. Are Your Data Privacy Strategies Ready?
Time is almost up for companies scrambling to get their data privacy strategies in compliance with the California Consumer Protection Act (CCPA). Beginning as early as July 1, 2020, the California Attorney General’s office can start enforcing the CCPA and handing out penalties of up to $2,500 per violation or up to $7,500 per intentional violation.
So, when exactly, will the CCPA become law? On June 1, 2020, the California AG took the final step before the regulations become enforceable by submitting the final text of the CCPA Regulations to the California Office of Administrative Law (the “OAL”). The OAL has 30 working days–plus an additional 60 calendar days related to the COVID-19 pandemic–to review the submission and approve it to become an enforceable law. Doing the math, the California AG can begin enforcing violations as early as July 1 or as late as September 1, 2020.
Strategies for Improving ERP CCPA Compliance
Companies using PeopleSoft, SAP ECC, S/4HANA and Oracle EBS are likely facing additional compliance challenges due to inherent limitations built into these legacy ERP systems. Let’s look at a couple of tactics for enhancing your ERP systems to improve compliance with CCPA and establishing the capabilities to prepare for the uncertainty around data privacy.
1: Enhance Visibility into User Activity
The CCPA requires organizations to implement appropriate security measures around personal data and satisfy data subject access requests (DSARs). That means businesses must know what personal data they store and the user activity going on around it. However, traditional ERP systems do not provide the required level of granularity.
To achieve detailed visibility around data usage, organizations need to expand their native logging capabilities by adopting a strategy that focuses on data access and usage. Meaning, organizations must capture contextual details like date of access, UserID, IP address, device, location of access, actions performed, etc.
This is information that is critical for compliance reporting and understanding how data is being used within your organization.
2: High Privilege Access Should be the Highest Priority for Strengthening DLP
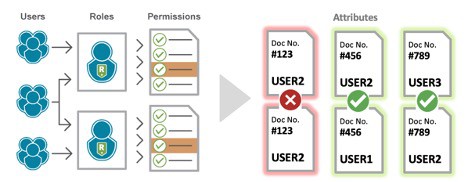
When it comes to ERP systems, the static rules that govern access can be limiting because roles and privileges are user-centric, not data-centric. User-centric roles say a person (or group in most cases) can view something under any circumstances, while data-centric means the nature of the data defines the access. This gets organizations in trouble time and time again from a DLP perspective because high privilege users always have the ability to see more data than they actually need (to do their job.) This makes non-compliance with CCPA almost inevitable. Overexposure of data is your biggest enemy and governing access by static rules (aka ‘all or nothing access rules’) creates an enormous liability.
Implementing data-centric policies (typically through attribute-based access controls) ensures that a user can only access data deemed necessary and job-related. This is because the data itself is governing access – not a user role. For example, access to certain high-risk transactions can be restricted based on a user’s location – or access can be granted, but with masked data fields. With every variation of context, attribute-based access controls can pivot and adjust accordingly. By reducing the threat surface, companies can reduce the risk of data leakage and mitigate compromised access damages.
3: Use Real-Time Analytics and Data Visualization (SEIM) to Expedite Incident Response Time
Integrated and real-time analytics displayed on dashboards were always a “nice-to-have” feature for security teams; however, keeping CCPA deadlines of breach identification and reporting in mind, data visualization has become a must-have feature. These advanced dashboards equip security professionals with real-time snapshots of data usage. The drill-down capabilities allow for enhanced data discovery and exploration to expedite breach detection and response, helping organizations stay compliant with CCPA and other existing and upcoming regulations.
Ready or Not, CCPA Enforcement Has Arrived
If you’ve not wrapping up your CCPA compliance efforts by now, there’s no better time than the present to start (or continue down that road). Appsian can help you fast track your compliance efforts by enhancing your visibly and applying a data-centric ERP compliance framework.
The last thing any company wants is to discover that they’re out of CCPA compliance only when there’s a breach of the regulation.
Contact us to learn how Appsian can help you address your end-to-end security and compliance needs.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Improve SAP Access Policy Management During These Turbulent Times – and Beyond
In these less than ordinary times, organizations are dealing with disruption at a frequency higher than ever before. An unfortunate side-effect of this COVID crisis has been its impact on employees. Whether furloughed, laid off, or set to take on broader responsibilities, change is happening. And naturally, these changes must be reflected in your ERP applications’ access policy management.
The uptick in user provisioning is placing additional pressure on SAP security and IAM teams, already burdened with securing remote access to applications for people working from home. These days, you have to wonder if IT professionals are feeling like they’re chasing something they can’t keep up with. And that leads to problems.
Joiners, Movers, and Leavers
The user provisioning process typically encompasses three phases: joiners, movers, and leavers. In short, they are three separate scenarios – when employees are onboarded, when they switch positions/departments internally, and when employees leave the organization. Given COVID, leaving the organization could mean either termination or furlough.
If overburdened IT and security teams cannot address provisioning promptly, organizations are leaving themselves open to an onslaught of risk in times where cyber-attacks are peaking and employees are already feeling stressed out.
Thanks to an enlarged threat surface from remote access, a compromised account can cause considerable damage before it is detected. Excessive privileges only multiply this risk. Alternatively, strained and disgruntled employees with excessive privileges may be tempted by fraud, especially in cases where segregation of duties (SoD) should be in play. If an employee was given extra responsibilities that necessitated new roles, potential conflicts might be overlooked.
Three Tips for Improving SAP Access Policy Management
Setting the roles is only one step. You don’t want to give everybody the same kind of visibility or access to data, depending on their role. This is a great time to invest in data security technology and establish more granular access policies. Here are three tips for improving your SAP access policy management:
1: Leverage Attribute-Based Access Controls (ABAC) to Simplify User Provisioning
Organizations with similar roles spanning multiple business units turn to role derivatives to ensure access is segmented appropriately. While effective from a control perspective, managing these roles can prove burdensome as the number of role derivatives multiply with each branch-off.
For example, a manufacturing organization has 50 functional roles shared by users across 10 different plants. Using role derivatives, they would end up managing 500 different roles to ensure access is segregated appropriately. The sheer scale can be overwhelming to your SAP security team to begin with – and now we’re adding in all the joiners, movers, and leavers from COVID-induced workforce changes.
The purpose of roles is to be scalable! We want access policies that are one-to-many, not one-to-one. To gain back simplicity and lighten the load on your IAM teams, organizations can extend their existing role-based access control (RBAC) model with attribute-based access controls (ABAC). ABAC allows you to easily bring fine-grained “attributes” into your authorization decisions. In the example above, one could go from managing 500 role derivatives down to 50 roles and 1 supplemental ABAC policy that can consider the differing factor, a user’s assigned plant code, to automatically segregate their access appropriately.
2: Reduce Your Attack Surface with Fine-Grained Entitlements
The Principle of Least Privilege is a crucial tenet in information security. The goal is to minimize risk by providing users with the minimum level of access needed to perform a task at hand. This is the purpose of existing role-based access controls – e.g., an HR manager should not have access to finance transactions because it is out of their scope. However, this does nothing to protect data within their scope. Should the HR manager have access to social security numbers or compensation data at all times? After hours? Remote? The answer is likely, no.
Organizations can reduce their amount of accepted risk by applying granular business policies and access controls to strengthen data-level and transaction-level security. Leveraging ABAC, you can enforce risk-aware controls to place limitations on what users can access within your application, from where, when, how they can access, and what they can do with data. ABAC provides an additional level of security by incorporating additional context like geolocation, time of day, and IP address. This ensures appropriate user access and prevents users from having more access than they need. Want sensitive data masked when access is outside your network? Done. Want to block high-risk transactions after hours? Easy.
3: Manage the Identity Lifecycle with User Activity Monitoring
Organizations should always engage in some kind of user activity monitoring, regardless of the number of joiners, movers, and leavers they’re dealing with. But this monitoring must extend beyond time-consuming and potentially expensive manual audits. You want to make sure the access control policies you’ve established are working and that you’re watching for anomalies. Some user activity to consider monitoring includes:
- Identifying high-privilege user activity and critical transactions while closely monitoring and auditing on a regular basis
- Continuously monitoring access across peer group activity for visibility into who changed what in regard to roles and permissions
- Setting risk-aware alerts such as location of user, device accessing network, etc. This monitoring is vital for streamlining threat detection and alleviating the manual process typically required for threat response
Assign Ownership and Responsibility Over User Provisioning
While you’re monitoring user activity, don’t forget to put some eyes on your IT and security teams. You’ll want to assign ownership and responsibility to whoever responds to access requests and reviews temporary team member access. Keep good records as to why approvals are made or changed. You’ll want to approach this in a way that is easily audited. (Tip: email is not that process).
Conclusion
There are many moving parts and people that IT staff and security teams must manage. Leveraging tools that can improve an organization’s SAP access policy management will go a long way towards protecting important data and easing the burden on stressed IT and security teams.
Schedule a demonstration today and learn how Appsian can mitigate SAP business risks with ABAC and User Activity Monitoring.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
How to Streamline the SAP Segregation of Duties Exception Process Using Attribute-Based Access Controls
Secure, compliant, and efficient business processes are critical to enterprise operations. In SAP, Segregation of Duties (SoD) is a key principle in making this possible.
What happens when an SoD exception is necessary?
Often times a user will need to be granted roles and privileges that pose a conflict of interest. It could be that an employee is part of a small department, or that a security clearance precludes others from involvement. Whatever the reason, this user needs the ability to handle multiple steps in a business process – and an exception is made.
Here’s where things can get tricky. Once an SoD exception is made, your standard preventive controls are no longer effective. This is one of the major shortfalls of SAP’s static, role-based access controls.
Shifting from a preventive approach to a detective approach…
… you must now gather access logs, filter out false-positives, and finally, send to the appropriate control owner to review and sign-off. Besides the additional overhead of manual reviews and approvals, detective controls create room for human error and increase the dwell time before red flags are caught.
So why are current SAP SoD Controls limited?
Without the logic ability to decipher potential violations from actual violations, preventive controls are a non-starter. Your (preventive) SAP access controls determine authorizations based on two things: 1.) a user’s role and 2.) the role’s associated permissions (think transactions.) While this works in the vast majority of cases, enforcing SoD requires controls with more granularity.
Let’s take a look at what an actual SoD violation entails
The whole objective of SoD is to avoid conflicts of interest in your business processes. Although, conflicting transactions do not necessarily pose a conflict of interest, unless the subject is the same.
For example, a user performs the transactions to create and approve multiple purchase orders. Looking at the transactions themselves, this activity has the potential for violations. Looking deeper into the PO details, you may see that the user never created and approved the same PO – therefore no violation was made.
SAP can show you 1.) the user and role, and 2.) the transactions performed, but is missing the 3rd component: the field-level values in the PO itself. This lack of visibility into attributes beyond roles and permissions is what makes preventive controls a non-starter and clutters SoD audit logs with false-positives when exceptions have been made.
The Solution? Enforcing SoD Policy with Attribute-Based Access Controls
Attribute-Based Access Controls (ABAC) enable the use of “attributes” in authorization decisions. These attributes can be anything from user details such as role, department, nationality, or even a user’s security clearance level. Additionally, access context such as IP address, location, time, device and transaction history can be considered. And most importantly for SoD, data attributes can now be used in authorization logic. This means that field-level values within SAP can be used to determine whether to block or allow a transaction, and these details can further be used in reporting activities.
In the Purchase Order example above, data attributes can be used to identify whether a user performed the first transaction and make the correlation that performing the second transaction would result in a violation.
Combining SAP’s role-based access controls (RBAC) with an attribute-based access control (ABAC) solution enables granular control and visibility that delivers a wide range of business benefits.
Newfound Flexibility in SoD Exception Scenarios – RBAC + ABAC Hybrid Approach
The RBAC + ABAC hybrid approach opens the possibility to apply preventive controls in SoD exception scenarios. By doing so, you can offer users the flexibility an exception provides while still preventing any actual violations from happening.
Together, this hybrid approach (RBAC + ABAC) enables a dynamic SoD model that prevents violations while still allowing the flexibility of conflicting roles to be assigned (when necessary) and reinforces role-based policy to mitigate over-provisioning.
RBAC + ABAC Hybrid Approach Using Appsian
Appsian adds an additional authorization layer to SAP GRC Access Control that correlates user, data and transaction attributes, along with identified SoD conflicts, to block conflicting transactions at runtime.
Contact Us to learn more about how a hybrid access control approach can strengthen Segregation of Duties (SoD) at your organization.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives