How Does Appsian Work with SAP GRC Access Control?
At the SAPinsider 2020 virtual conference experience, one of our product demo attendees asked how Appsian works with SAP GRC Access Control. We get this question a lot as SAP security and system professionals explore adding attribute-based access controls (ABAC) to the native SAP role-based access controls (RBAC) to streamline and strengthen access policy management and enforcement. Sometimes there is confusion about whether ABAC is enhancing or replacing their RBAC. Let’s take a quick look at how Appsian’s ABAC works with and enhances SAP GRC Access Control.
What is SAP GRC Access Control
Organizations use SAP Governance, Risk, and Compliance (SAP GRC) to manage regulations and compliance and remove any risk in managing critical operations. One of the SAP GRC modules that helps organizations meet data security and authorization standards is SAP GRC Access Control. This module ensures that the right access is given to the right people with RBAC. It uses templates and workflow-driven access requests and approvals to streamline the process of managing and validating user access and provisioning. Without SAP GRC, for comparison, a person is creating all the roles from scratch and assigning privileges to them.
Appsian Enhances SAP GRC with Attribute-Based Access Controls
Appsian combines the SAP GRC role-based access controls with an attribute-based access control solution that delivers an ABAC + RBAC hybrid approach. This enhanced approach enables granular control and visibility that delivers a wide range of business benefits and lets you deploy data-centric security policies that leverage the context of access to reduce risk.
Appsian overcomes the limitations of traditional RBAC, allowing you to fully align SAP security policies with the objectives of your business and streamline audits and compliance.
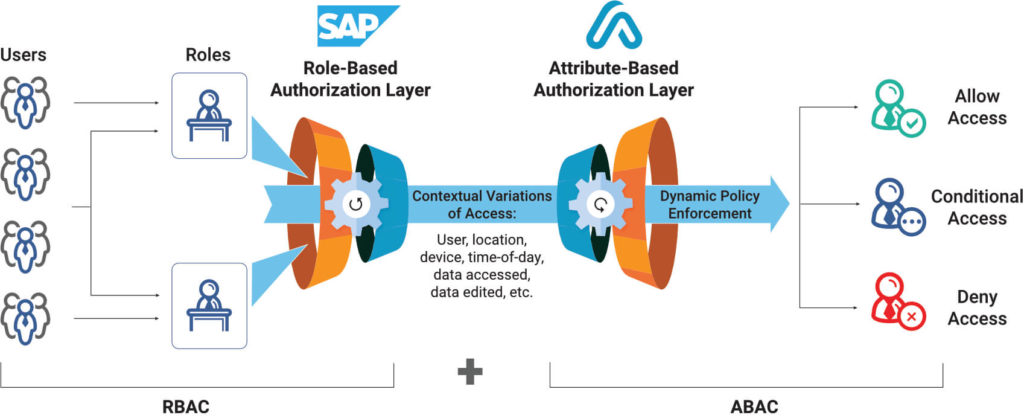
As you can see in this illustration, ABAC begins the moment users start to access data and transactions. Where RBAC assigns access based specific roles, ABAC considers the context of access (who, what, where, when, and how) before allowing access to transactions or data. Customers can set up additional rules that allow conditional access, for example, masking specific data fields or limiting the number of transactions after a particular time of day) or entirely denying access based on factors such as an unknown IP address.
Real-Time Analytics for SAP Security & Risk Management
With Appsian360, our real-time analytics and reporting tool, Appsian can enhance the SAP GRC reporting capabilities with direct, real-time visibility into transaction usage, violations, and compliance risk. Additionally, customers can:
- Monitor transaction usage, master data changes, and SoD violations
- View actual SoD violations with user, data, and transaction correlation
- Segment reports by user/data attributes
- Drill down into end-user usage events
Appsian360 provides analytical reports to drill down into end-user usage events to capture business risks and anomalies, and usage events that tie back to compliance risks.
The ABAC + RBAC Hybrid Approach to SAP GRC Access Control
By combining data-centric security capabilities with attribute-based policies, Appsian extends and enhances the existing SAP GRC internal access controls and improves the reporting and auditing capabilities.
Contact us today and schedule a demo to see how Appsian can help you enforce access controls beyond the standard RBAC model of SAP.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives
Improve SAP Access Policy Management During These Turbulent Times – and Beyond
In these less than ordinary times, organizations are dealing with disruption at a frequency higher than ever before. An unfortunate side-effect of this COVID crisis has been its impact on employees. Whether furloughed, laid off, or set to take on broader responsibilities, change is happening. And naturally, these changes must be reflected in your ERP applications’ access policy management.
The uptick in user provisioning is placing additional pressure on SAP security and IAM teams, already burdened with securing remote access to applications for people working from home. These days, you have to wonder if IT professionals are feeling like they’re chasing something they can’t keep up with. And that leads to problems.
Joiners, Movers, and Leavers
The user provisioning process typically encompasses three phases: joiners, movers, and leavers. In short, they are three separate scenarios – when employees are onboarded, when they switch positions/departments internally, and when employees leave the organization. Given COVID, leaving the organization could mean either termination or furlough.
If overburdened IT and security teams cannot address provisioning promptly, organizations are leaving themselves open to an onslaught of risk in times where cyber-attacks are peaking and employees are already feeling stressed out.
Thanks to an enlarged threat surface from remote access, a compromised account can cause considerable damage before it is detected. Excessive privileges only multiply this risk. Alternatively, strained and disgruntled employees with excessive privileges may be tempted by fraud, especially in cases where segregation of duties (SoD) should be in play. If an employee was given extra responsibilities that necessitated new roles, potential conflicts might be overlooked.
Three Tips for Improving SAP Access Policy Management
Setting the roles is only one step. You don’t want to give everybody the same kind of visibility or access to data, depending on their role. This is a great time to invest in data security technology and establish more granular access policies. Here are three tips for improving your SAP access policy management:
1: Leverage Attribute-Based Access Controls (ABAC) to Simplify User Provisioning
Organizations with similar roles spanning multiple business units turn to role derivatives to ensure access is segmented appropriately. While effective from a control perspective, managing these roles can prove burdensome as the number of role derivatives multiply with each branch-off.
For example, a manufacturing organization has 50 functional roles shared by users across 10 different plants. Using role derivatives, they would end up managing 500 different roles to ensure access is segregated appropriately. The sheer scale can be overwhelming to your SAP security team to begin with – and now we’re adding in all the joiners, movers, and leavers from COVID-induced workforce changes.
The purpose of roles is to be scalable! We want access policies that are one-to-many, not one-to-one. To gain back simplicity and lighten the load on your IAM teams, organizations can extend their existing role-based access control (RBAC) model with attribute-based access controls (ABAC). ABAC allows you to easily bring fine-grained “attributes” into your authorization decisions. In the example above, one could go from managing 500 role derivatives down to 50 roles and 1 supplemental ABAC policy that can consider the differing factor, a user’s assigned plant code, to automatically segregate their access appropriately.
2: Reduce Your Attack Surface with Fine-Grained Entitlements
The Principle of Least Privilege is a crucial tenet in information security. The goal is to minimize risk by providing users with the minimum level of access needed to perform a task at hand. This is the purpose of existing role-based access controls – e.g., an HR manager should not have access to finance transactions because it is out of their scope. However, this does nothing to protect data within their scope. Should the HR manager have access to social security numbers or compensation data at all times? After hours? Remote? The answer is likely, no.
Organizations can reduce their amount of accepted risk by applying granular business policies and access controls to strengthen data-level and transaction-level security. Leveraging ABAC, you can enforce risk-aware controls to place limitations on what users can access within your application, from where, when, how they can access, and what they can do with data. ABAC provides an additional level of security by incorporating additional context like geolocation, time of day, and IP address. This ensures appropriate user access and prevents users from having more access than they need. Want sensitive data masked when access is outside your network? Done. Want to block high-risk transactions after hours? Easy.
3: Manage the Identity Lifecycle with User Activity Monitoring
Organizations should always engage in some kind of user activity monitoring, regardless of the number of joiners, movers, and leavers they’re dealing with. But this monitoring must extend beyond time-consuming and potentially expensive manual audits. You want to make sure the access control policies you’ve established are working and that you’re watching for anomalies. Some user activity to consider monitoring includes:
- Identifying high-privilege user activity and critical transactions while closely monitoring and auditing on a regular basis
- Continuously monitoring access across peer group activity for visibility into who changed what in regard to roles and permissions
- Setting risk-aware alerts such as location of user, device accessing network, etc. This monitoring is vital for streamlining threat detection and alleviating the manual process typically required for threat response
Assign Ownership and Responsibility Over User Provisioning
While you’re monitoring user activity, don’t forget to put some eyes on your IT and security teams. You’ll want to assign ownership and responsibility to whoever responds to access requests and reviews temporary team member access. Keep good records as to why approvals are made or changed. You’ll want to approach this in a way that is easily audited. (Tip: email is not that process).
Conclusion
There are many moving parts and people that IT staff and security teams must manage. Leveraging tools that can improve an organization’s SAP access policy management will go a long way towards protecting important data and easing the burden on stressed IT and security teams.
Schedule a demonstration today and learn how Appsian can mitigate SAP business risks with ABAC and User Activity Monitoring.
Put the Appsian Security Platform to the Test
Schedule Your Demonstration and see how the Appsian Security Platform can be tailored to your organization’s unique objectives












